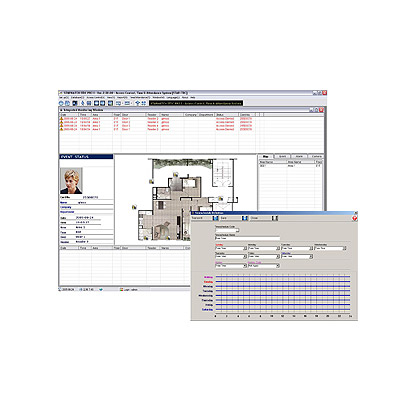
Access Control Softwares (653)

Stand-alone deployment, with own map viewer and alarm & event viewer, or as integral part of a video management system (e.g. BVMS) Combines high-end access control features, performance and availability with intuitive operation Highly scalable Easy to configure Situation always under control for doors, elevators, car parks and visitors, with alarm list and for different threat scenarios Centralised user and event management of intrusion panels Comprehensive security management: Integrates with intrusion and video systems Robust and Secure: Multi-level architecture for system reliability, comprehensive data security and privacy protection
Add to Compare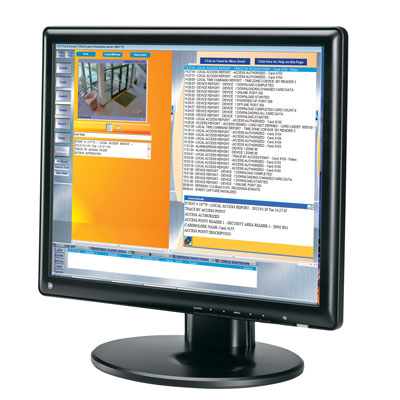
Topaz TPZ-SYS-D-GE is a four-reader system that allows access control, video surveillance, alarm monitoring, and photo ID badging with the Topaz Access Control System. It is packaged with everything you need to get your security system up and running quickly and reliably.
Add to Compare
Ideal for large and/or geographically widespread installations Offers scheduled access, auditing, reporting, email notification of events, key expirations, blocking a lost key, and multiple key and delayed access Manage as many as 15,000 locks and 15,000 keys Spread responsibility through a hierarchy of administrators Share lock access with other Enterprise systems Grant emergency one-time access or program and download keys in the field for on-demand access Schedule missions Time zone flexibility Integrate with other software applications Grouping capabilities for locks and people Access through a LAN or securely over the Internet
Add to Compare
Borer has released Fusion SE, a PC based access control software package for users of small-to-medium access control systems. Fusion SE Access Control Software runs on a PC workstation operating under Windows XP, Vista and Windows 7. Fusion SE provides similar functionality to the Enterprise and Profession versions of Fusion. The Fusion SE software is free and there are no restrictions as to the numbers of doors you can connect to the system or the number of people you are entitled to enrol onto the Fusion database. The system is made easy to deploy because all door controllers and field devices communicate with the PC hosting Fusion software via the users LAN and structured cabling infrastructure. It is also simple to commission as new field devices (card readers and controllers) log on and self configure on power up. Fusion has an intuitive easy-to-use GUI and Wizard style operator interface enabling full management and control of the Security Access System. Fusion supports many combinations of access level and time zone operation. It supports both profile and role based access rules making the planning, administration and management of access rights simpler. Fusion provides the operator with a comprehensive set of tools to support the remote operation of door locking/unlocking and alarm setting and resetting. In addition a powerful field Programmable Scripting Engine enables Fusion to support the integration of Camera and Intruder systems to access control enabling many complex functions, such as out-of-hour key holder access, to be supported on even the most basic system. Uniquely, in the security industry, the delivery of power to field devices, door controllers and door locks is controlled and monitored by the Fusion software. This enables users to monitor and manage the energy consumed by each door lock and door controller connected to the system providing cost savings amounting to tens of pounds per door per year. Fusion also provides a graphical view of almost every element of the system down to the status of each individual input such as a magnetic door monitor or tamper sensors. This is an invaluable aid for both on-site and remote over the Internet problem identification and solving.
Add to Compare
An access control system for stand-alone application or for integration with other systems, such as the Bosch video management system BVMS or Bosch B and G series intrusion panels As a stand-alone system, it features a simple-to-use map and alarm viewer for a rapid assessment of all the devices and entrances on the site As an integrated system, it allows the operator of a video management system to perform door-related tasks like video-based ID verification, to grant and deny access, or to disable doors Intrusion areas can be armed directly from the Map View, and intrusion panel users can be centrally managed Combines high-end access control features, performance and availability with intuitive operation Web-based visitor management Comprehensive security management: Integrates with intrusion and video systems Highly scalable Easy to configure Easy to use: Intuitive GUI for maps and alarm viewer
Add to Compare
Stand-alone deployment, with own map viewer and alarm & event viewer, or as integral part of a video management system (e.g. BVMS) Combines high-end access control features, performance and availability with intuitive operation Highly scalable Easy to configure Situation always under control for doors, elevators, car parks and visitors, with alarm list and for different threat scenarios Centralised user and event management of intrusion panels Comprehensive security management: Integrates with intrusion and video systems Robust and Secure: Multi-level architecture for system reliability, comprehensive data security and privacy protection
Add to Compare
In today's multilingual society, many of the access control and time & attendance management software users request the software to be translated into different language other than English. IDTECK's professional access control and time & attendance management software line-ups, STARWATCH STANDARD, STARWATCH TIME PRO and STARWATCH ENTERPRISE, are based on Unicode structure, which allows the users to directly enter text for all the scripts in their own languages. It does not require additional patch or downloads to enter and render the texts of the scripts as it flawlessly processes, stores and renders multilingual texts. In management systems such as this, it makes it easy to convert one language to another language, even for one of a kind, rarely used, distinctive language. In return, it eliminates the complicated process of learning some new software to convert languages in the software.STARWATCH STANDARD is efficient access control and time & attendance management software, suitable for small and medium sized business. This user-friendly software includes setup wizard and diagram function for easy installation and provides helpful tool tip information to increase the user convenience. The software guarantees flawless compatibility with all of IDTECK's standalone and network access controller.Specialized for extensive time & attendance management, STARWATCH TIME PRO is a perfect solution for all your HR administration needs. Not only it ensures accurate time and attendance management, but also keeps track of overtime work, multi-shift, and various work rules to accommodate any kind of work environments. STARWATCH TIME PRO is equipped with various report generation feature, which is also available on the web browser for viewing and printing.STARWATCH ENTERPRISE boasts advanced security integration as the powerful software security features has been maximized to enhance the efficiency and high-level security with easy operation and management of the large sized enterprises. This top of the line management software is capable of controlling and managing multiple buildings and sites in different locations via LAN or WAN communication.Long experience in biometric access control and time & attendance field, IDTECK products assure the most reliable technology out in the security market. IDTECK offers wide range of security products, to provide the best security solution to suit your needs. All of IDTECK products are certified by UL, CE, FCC, MIC, and RoHS to satisfy the standards for international exports.
Add to Compare
Apollo Security will be demonstrating advanced Universal Video Integration, OPC support, FIPS 201 and TWIC support at ISC West. Contact Apollo if you would like to schedule a private demonstration of these developments.Among the products on show will be Apollo Security's APACS software. The APACS software is designed for Apollo-based integrated security systems. It provides management of the access control system and performs information exchange and coordination between all subsystems, including: alarm monitoring, fire protection, analogue / IP live and recorded video, HVAC, paging, lighting, elevator control, visitor management and badging. In addition, APACS also provides data exchange with third party human resources, time and attendance and visitor management packages. Using PC with the Windows based operating system; APACS effectively performs in both small single computer systems and large-scale integrated client-server systems using TCP/IP protocol. In multi-user applications a powerful computer is used as a dedicated database server to process queries from all APACS workstations. Users can select between Firebird, Interbase, Oracle and MS SQL databases. APACS software is available in three packages: Pro, Standard and Lite. APACS Lite provides basic reliable access control. If features text-based on-line event display, alarm linkage on hardware level, event retrieval and sorting, elevator control and other functions.APACS Standard includes graphic maps, alarm display, live video, hardware status tree and badging.APACS Pro is an advanced security management software package. It integrates access control with digital and analogue video equipment, visitor management systems, HVAC and lighting control systems, public announcement and paging systems. Distinctive feature of APACS Pro is built in reaction mechanism. Any event, time zone, card or PIN read can trigger a reaction. Possible reactions can be DVR/CCTV control by signals from readers or alarm inputs, HVAC and lightning system control by time zones, audible alarms to operator, transmission of alarm messages to pagers, roll call, execution of external programs or activation of external systems. Reactions can be unconditional - immediate response to specified event, or conditional - an operator will be prompted with a list of possible reactions; default reaction will be executed if operator does not respond to the prompt. Reaction mechanism removes some of the operator workload and increases security, ensuring that important events will be noted. For example, APACS Pro can automatically arm the building as the last person leaves, and turn on the lights and air conditioning as the first person is granted access in the morning, or it can be configured so that personnel can use a special PIN (i.e. 911) to notify guards of emergency situations from the nearest reader with a keypad.Other APACS Pro features include live video verification, roll call and extended personnel reports. With its flexible modular structure, user friendly design, single and multi-user capabilities, and three different options, APACS can provide a solution that meets the customer's requirements today and in the future. The APACS software package consists of six modules: Alarm Mode, System Configuration, Cardholder Database, Report Generation, Visitor Management Web Interface, and External Reports. This special modular structure provides additional security and convenience by distributing tasks to difference operators. The systems can be monitored, controlled and configured from any workstation, provided the required module is installed and the operator has the appropriate permission.Features:Windows 2000/XP/2003/Vista/Windows 7 operating systemsFirebird, Oracle or MS SQL (including MS SQL 2008) database management systemSingle and multi-user applicationsMore than 50 workstationsIntuitive, user-friendly interfaceUnrestricted number of controllers, readers, and alarm panelsModular structureMultiple card formatsOnline help255 access levels, 6 access levels per card, individual access levels (precision)Elevator ControlDuress communicationDatabase conversion utilities
Add to Compare
OnGuard Visitor is a dependable and cost effective visitor management application that enables an organization to manage and track visitors throughout its facilities, using standard desktop technology. Whether it is implemented as a standalone system or seamlessly integrated with other OnGuard application modules to create a total security management environment, OnGuard Visitor offers unlimited flexibility by allowing IT and security managers to further capitalize on existing IT investments in their facilities.
Add to Compare
Morse Watchmans KeyPro III Key Control Software maximises key management system with user-friendly KeyPro key control software. It establishes permission levels for each User Code and monitor data from any desktop connected to the network. It can run activity reports, sort based on different criteria, view and print reports, and more. It canl also generate practical management reports, which trace key movements by time, date and user code. An audit trail report indicates the time and date of every key accessed by a user for a given time parameter.
Add to Compare
Advanced, scalable visitor management system Web client software compatible with the latest browsers Supports any computing device with browser and internet Full functionality on tablet and smart phone devices Suitable for visitors, contractors and visiting employees Integrates to Outlook and Google mail systems On-line record of all previous visits Retains visitors photo with configurable expiration date User defined fields for any data collection Supports USB or tablet webcams for photo capture Touch-screen self-registration capability Multi-tenant building capabilities Supports standard visitor badge printers Supports drivers license and passport scanners Optionally integrates with AMAG Symmetry software Simple import of employee details using spreadsheets
Add to Compare
Net2 software is designed to run on a PC with a Windows 2000 or XP operating system. It is designed to feel immediately familiar to any Windows user. It will organise and report on up to 10,000 users and hundreds of doors. Net2 standard software contains all of the basic access control features to control access privileges and report on users. Other features include multiple workstations, TCP/IP camera integration and remote sites using TCP/IP or modems. Net2 professional software contains all of the features of Net2 standard software with the addition of fi re alarm integration, roll call/muster reporting, anti-passback and Timesheet.
Add to Compare
Distributed access control system with graphical alarm management Seamless integration and interaction with video, fire, intrusion and PA/VA systems via the common BIS platform High resilience thanks to a 4-tier system architecture and redundancy of critical components Integration of third-party products via open and secure protocols and SDK Efficient enrollment process that makes onboarding faster and more secure
Add to Compare
Biometric, Photo ID, Visitor Management, Time & Attendance, Elevator Control, Central / Remote Monitoring, Import/Export of Information, Multiple Tenants / Partitioning, Windows XP Pro; Windows 2000, Windows Server 2000 / 2003
Add to Compare
Lenel has partnered with ActivIdentity to jointly market a solution for physical access to facilities and logical access to networks. The joint solution offers many benefits, including increased security and lower total cost of operation. In addition, the Lenel-ActivIdentity solution will be a primary component for a corporation’s efforts to achieve compliance with regulations such as Sarbanes-Oxley and HSPD-12. The ActivIdentity Enterprise Access Card consolidates employee logical credentials onto a single, secure smart card. This provides a photo ID as well as a security device that enables secure Windows and network login, PC 'locking', secure remote access (VPN), secure email with digital signatures, and single sign-on to enterprise and desktop applications.The Lenel OnGuard® ID CredentialCenter™ application consolidates employee physical credentials, biometrics, and demographic information onto a single secure smart card, captures photo ID and prints the card. The Lenel OnGuard security platform offers seamlessly integrated access control, alarm monitoring, identity management, digital video, intrusion detection, asset management, card production, and visitor management.The joint solution integrates the issuance and administration of cards and credentials for both physical and logical domains, and combines a photo ID, smart card and proximity card onto a single, easy to use device. With the importance of physical and logical security, the integration of the Lenel and ActivIdentity products allows complete life cycle management of the credential.See the ActivIdentity Architecture diagram
Add to Compare
Access PE provides self contained access control for small and medium-sized companies. Its installation is extremely simple and fast. There is no need to install and administer a database system. The system is easy to use and enables a person with minimal training to create badges and administer access rights in a very short time. Specific event logging and reporting allows you to trace who was when and where on your company’s grounds.
Add to Compare
The AC2000 Visitors module offers a comprehensive visitor management solution that is fully integrated with the CEM AC2000 SE (Standard Edition) access control system. The Visitors application provides a powerful tool to monitor and control access for temporary cardholders (visitors).
Add to Compare
Access control and basic Time & Attendance management software. Upload and download of card data, lock type, door open time and sensor operation data. Real-time monitoring of event/alarm. Data upload and download. Dynamic report generation (Group, Card, Event Result, Signal). Database restoration and backup. Compatible controller: 100R.
Add to Compare
Keyscan K-DSC is a System VII software module for DSC Power series and Maxsys intrusion panel integration. Observe and control entire access and intrusion systems through one integrated software package. Add, delete, and modify individual’s DSC passcodes all through System VII. Active logging of all DSC panel activity, arming, disarming, alarm conditions and much more. Run reports on the entire building system, including all access activity and DSC panel activity. Provides real-time display of DSC system, zone and partition status.
Add to Compare
Allows system users to make use of smartphone or smartwatch in place of electronic tokens or traditional keys with a Paxton10 system Utilising the built-in Bluetooth® wireless technology in Paxton10 readers, your smart device can securely communicate with the Paxton10 system to grant or deny access through any Paxton10 door This Bluetooth® access control solution makes access management simple and convenient Paxton Key also enables the user to carry out predefined building management functionality, such as setting the intruder alarm, simply by presenting their smart credential
Add to Compare
Access PE provides self contained access control for small and medium-sized companies. Its installation is extremely simple and fast. There is no need to install and administer a database system. The system is easy to use and enables a person with minimal training to create badges and administer access rights in a very short time. Specific event logging and reporting allows you to trace who was when and where on your company’s grounds.
Add to Compare
CEM SWINT - INTEGRA AC2000 Satel Integra alarm interface enables alarms from Integra alarm panels to be fully integrated with the AC2000 access control system. This enables AC2000 to act as the central Security Management System. The interface enables inputs from intruder panels to be placed as icons on the AC2000 AED (Alarm Event Display) application. This provides, on a single screen, a graphical representation of the physical layout of intruder sensors and allows for central alarm monitoring of both access control and intruder alarms.
Add to Compare
PCSC offers the EasyLobby Secure Visitor Management solution that allows organisations to automate the entire process of registering a visitor, printing a badge and capturing detailed information in seconds by simply electronically scanning an ID (such as a driver’s license, business card or passport). The solution is flexible, customisable and feature-rich to meet the needs of small and enterprise organisations with diverse visitor management processes and policy requirements.
Add to Compare
Monitoring and alarm management all on a single screen. Operational state and alarm state displayed for site items. Change the state of an item, (i.e. change access mode, open door, arm or disarm). Run a pre-configured report or reports from a selected site item, (i.e. view the cardholders that passed through a door, or any event activity or statistics for the item). View footage from one or more cameras associated with a site item. View live footage or footage in response to an alarm. Panning and zooming provides improved navigation around larger site plans. Operators have the ability to search for items on a site plan, or navigate directly to items in alarm. The flexibility in configuration allows for minimising clutter (*not just clutter but superfluous information/overrides), working alongside the privilege model means operators won’t be distracted with options that are not configured or they do not have the authority to use.
Add to Compare
CEM SWNVR-EX AC2000 exacqVision interface enables AC2000 to act as a flexible and fully integrated Security Management System. It provides the ability to define video alarm actions, view live footage as alarms occur and control cameras and run camera presets. The AC2000 DVR Video Configuration module seamlessly integrates AC2000 with exacqVision Video Management System servers. This will give operators the ability to define video alarm actions, search alarm feeds and playback recorded video from alarms.
Add to Compare
An access control system for stand-alone application or for integration with other systems, such as the Bosch video management system BVMS or Bosch B and G series intrusion panels As a stand-alone system, it features a simple-to-use map and alarm viewer for a rapid assessment of all the devices and entrances on the site As an integrated system, it allows the operator of a video management system to perform door-related tasks like video-based ID verification, to grant and deny access, or to disable doors Intrusion areas can be armed directly from the Map View, and intrusion panel users can be centrally managed Combines high-end access control features, performance and availability with intuitive operation Web-based visitor management Comprehensive security management: Integrates with intrusion and video systems Highly scalable Easy to configure Easy to use: Intuitive GUI for maps and alarm viewer
Add to Compare
CEM Systems will unveil for the first time at IFSEC AC2000 v6.3 software which includes the new "AC2000 Web" applications including the ‘Web Visitor’ application which allows visitor requests to be scheduled and managed via the web. CEM will also exhibit readers to combat card cloning including the new highly secure, yet cost-effective sPass DESFire smart card reader and DCM 350 two-door controller. Industry leading Power over Ethernet Plus (PoE+) access control solution from CEM will be on display along with CEM’s range of intelligent readers and biometric. At IFSEC AC2000 security management system will be integrated with American Dynamics video and DSC intrusion products, showing its seamless integration capabilities. AC2000 SE v.6.3 AC2000 SE v6.3 has many new features including AC2000 web applications and support for DSC PowerSeries intruder panels and American Dynamics latest video products, such as Hybrid-DVR (HDVR), videoEdge NVR4 and integration with the powerful victor unified solution.AC2000 web applications enable customers to access a hot of AC2000 SE applications via a standard web browser without having to install dedicated AC2000 software.Other features include the AC2000 Getting started Wizard, Personnel CSV Import Tool and Zone Occupancy for use in car parks and other suitable areas.sPass DESFire smart card reader and DCM 350 two-door controllerWith the threat of card cloning and the vulnerabilities of Wiegand controller signal cloning growing stronger, CEM have released the new sPass reader and DCM 350 two-door controller with secure RS485 encrypted communications to combat these threats and vulnerabilities.CEM sPass reader is a contactless smart card reader with powerful 3DES (Triple DES) encryption. Available as a keypad or non-keypad option, the sPass reader connects to the new DCM 350 intelligent two-door controller, which utilises highly encrypted RS485 communications to the sPass reader.CEM has also introduced a new contactless 13.56 MHz DESFire smart card to eliminate the threat of card cloning. Each card has different sets of encrypted keys that are securely stored on the card for high levels of security.Combined as one highly secure DESFire controller solution, the CEM eDCM 350 two-door controller, sPass DESFire reader & smart-card will offer the security market a low cost, yet highly secure option.CEM industry firstsCEM Systems designs high quality, innovative security solutions. With a culture for innovation, CEM consistently leads the industry in the development of its product range. Portable ‘hand-held' card readers Industry's only Airport specific access control system Ethernet based IP card readers Fully integrated biometrics Power over Ethernet Plus (PoE+) door control - simplifying installation and reducing project costsVisit CEM System at IFSEC- Tyco stand D10/E10, hall 5
Add to Compare
For Net2 and Paxton10 Makes remote site management more simple and flexible from any location Features a brand-new design, easy site search functionality, and improved biometric login Manages multiple sites remotely from a smartphone, tablet, or browser Includes the ability to secure the site at the touch of a button, open doors remotely from any location or set doors to lock and unlock during specified time periods, add, delete and edit users, quickly establish where users are in the event of an emergency and view default reports live or from the last 365 days
Add to Compare
Access PE provides self contained access control for small and medium-sized companies. Its installation is extremely simple and fast. There is no need to install and administer a database system. The system is easy to use and enables a person with minimal training to create badges and administer access rights in a very short time. Specific event logging and reporting allows you to trace who was when and where on your company’s grounds.
Add to Compare
Enables basic LDAP authentication for selected administrator logins When enabled, CyberAudit can optionally validate the administrator’s login and password against the LDAP server, rather than locally from within CyberAudit Software CyberAudit supports the LDAP method of sending the user name and passwork to the LDAP server via SSL on port 636. It does not support proxies or port forwarding to establish the LDAP connection
Add to Compare
Replicates data maintained in a primary database (e.g. human resources database) in the Gallagher database. Allows migration of existing cardholder details from an obsolete security system over to the Gallagher system. Enables mapping of existing employee fields (e.g. personal details, group memberships, licenses etc.) to their Gallagher Command Centre equivalent (e.g. personal data fields, access groups, competencies etc). Allows mapping between systems of 1:1 or 1:many relationships Allows third party data used in the external system to be translated to more meaningful descriptions on import to the Gallagher system. Provides manual one-off migrations of cardholder data to the Gallagher database and/or automatically updates when triggered by changes made in a primary employee database.
Add to Compare
OnGuard Multi-Server Enterprise for Microsoft Windows 2000 Server is the industry’s first multi-server, synchronized database solution designed for use by enterprises that have multiple facilities in multiple geographical locations. OnGuard Multi-Server Enterprise enables corporate security and IT managers to have central control over the entire integrated security system. At the same time, regional offices are able to maintain independence and operate their individual regional security systems autonomously.
Add to Compare
CEM SWHDVR-AD AC2000 American Dynamics HDVR interface provides the ability to associate access control alarms with digital video clips and to view live camera footage. This enables AC2000 to act as the central Security Management System. The AC2000 Video Configuration module seamlessly integrates AC2000 with the HDVR, giving the operator a range of facilities to generate alarm reports with recorded video playback. The high level two-way interface allows a user to fully integrate the power of an American Dynamics HDVR video system into the central AC2000 AED (Alarm and Event Display) application.
Add to Compare