Access Control Softwares (653)

Replicates data maintained in a primary database (e.g. human resources database) in the Gallagher database. Allows migration of existing cardholder details from an obsolete security system over to the Gallagher system. Enables mapping of existing employee fields (e.g. personal details, group memberships, licenses etc.) to their Gallagher Command Centre equivalent (e.g. personal data fields, access groups, competencies etc). Allows mapping between systems of 1:1 or 1:many relationships Allows third party data used in the external system to be translated to more meaningful descriptions on import to the Gallagher system. Provides manual one-off migrations of cardholder data to the Gallagher database and/or automatically updates when triggered by changes made in a primary employee database.
Add to Compare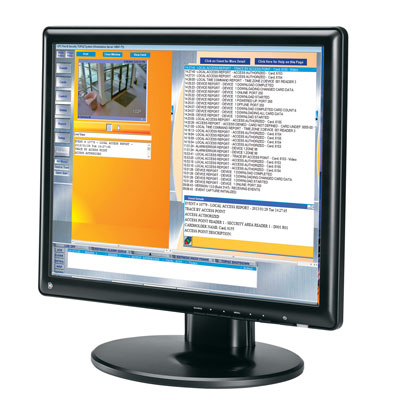
Topaz TPZ-SYS-B-GE is a two-reader system that allows access control, video surveillance, alarm monitoring, and photo ID badging with the Topaz Access Control System. It is packaged with everything you need to get your security system up and running quickly and reliably.
Add to Compare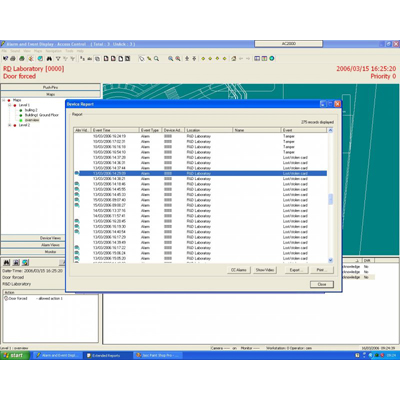
CEM SWVINT-MOBO AC2000 Mobotix interface provides the ability to associate access control alarms with Mobotix digital video clips. This enables AC2000 to act as the central Security Management System. The video interface seamlessly integrates AC2000 with Mobotix cameras, giving the operator a range of video imaging facilities to generate alarm reports with recorded video playback. The interface also allows system operators to view live video feed and control the camera’s view and run presets.
Add to Compare
CEM SWNVR-IV AC2000 IndigoVision NVR interface provides the ability to associate access control alarms with IndigoVision NVR digital video clips. This enables AC2000 to act as the central Security Management System. The AC2000 DVR Viewer module seamlessly integrates AC2000 with IndigoVision NVR, giving the operator a range of video imaging facilities to generate alarm reports with recorded video playback. The interface also allows system operators to view live video feed and control camera positioning. The system allows a user to fully integrate the power of a IndigoVision NVR video system into the central AC2000 Alarm Event Display (AED) application. AED enables all alarms, events and associated camera footage to be displayed centrally on the AC2000 system.
Add to Compare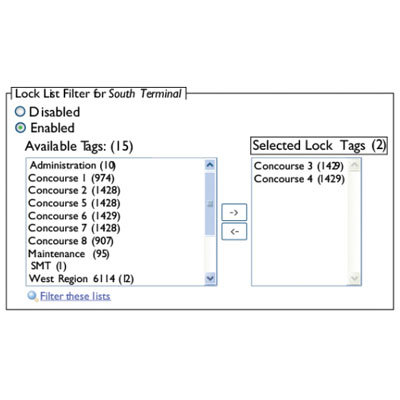
Enables limiting the number of locks loaded into Keys on a per communicator basis. This is needed when a legacy CyberKey requires individual permission to more than maximum 3300 lock capacity With this enhancement, keys and missions may effectively be granted access to an unlimited number or individual locks with each communicator in the system filtering the locks to selected tags Required to enable the improved 12,000 lock capacity in G2 CyberKeys
Add to Compare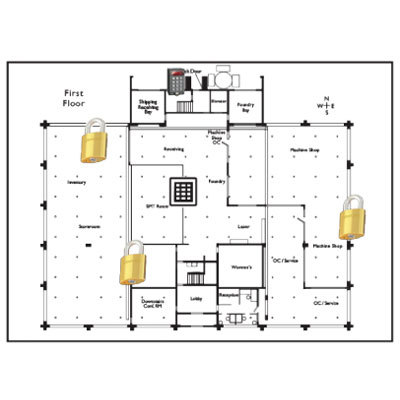
Opens a visual interface tool that allows CyberLocks and Communicators to be graphically “placed” on drawings, pictures, or maps (JPEG, PNG, or TIFF compatible) Helps large and geographically spread-out CyberLock deployments to improve tracking and locating of locks and communicators A landscape view allows to locate CyberLock devices in multiple locations. To view a specific location, simply click and zoom in. Maps and photos can be uploaded An embedded floor plan graphic allows to locate CyberLock devices within a specific location. To view a specific device, simply click and zoom in. By viewing the floor plan you can spot ‘holes’ in access control implementations An embedded photo may display individual lock placements. Both horizontal and vertical images can be uploaded
Add to Compare
Parabit 200-50007 is a multi-site database management/diagnostic software. It enables users to remotely manage and programme the ACS-1E control panels. It is based on Microsoft SQL and communicates over TCP/IP.
Add to Compare
The OnGuard Access integrated access control and alarm monitoring system delivers maximum protection, versatility, simple operation and cost efficiency. OnGuard Access incorporates the most advanced technologies available, including modern object-oriented software, an advanced client/server database architecture and Microsoft’s multitasking, multithreading 32-bit Windows 2000/XP operating system.
Add to Compare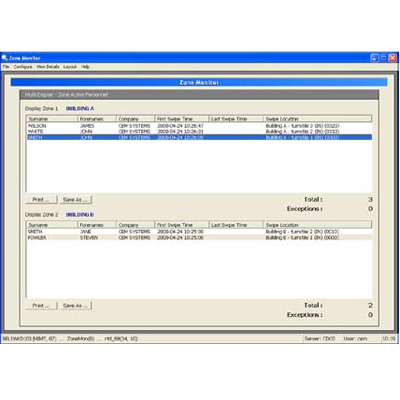
AC2000 Zone Monitor allows a real time view of all cardholder movements in defined zones. Zone Monitor provides up to date information on who is present on site for safety and security reasons and offers a real time display / numerical counter of every individual in a pre-defined zone within the building / site.
Add to Compare
Gallagher’s Action on Access solution allows a badge at a nominated reader to enable or disable access (card, competency, or access group membership) immediately or in the future, providing the ability to set sophisticated access rules using simple actions.
Add to Compare
Stand-alone deployment, with own map viewer and alarm & event viewer, or as integral part of a video management system (e.g. BVMS) Combines high-end access control features, performance and availability with intuitive operation Highly scalable Easy to configure Situation always under control for doors, elevators, car parks and visitors, with alarm list and for different threat scenarios Centralised user and event management of intrusion panels Comprehensive security management: Integrates with intrusion and video systems Robust and Secure: Multi-level architecture for system reliability, comprehensive data security and privacy protection
Add to Compare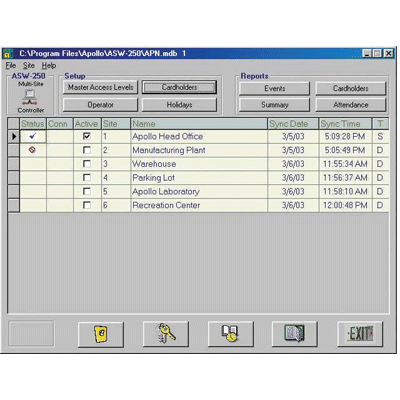
Support up to 4 controllers (APN-35) per site. 8 access levels per controller. Master access levels configuration. Real time reader mode display and control. Real time controller status display. Real time on-line events display. Selective events report generator. Time and Attendance Cardholder report. Access summary report. TZ input masking. Custom report headers. Stores additional notes about cardholder. Archiving utility. Customised card formatting. Virtually, unlimited access levels configuration. Creates clear, concise and filtered reports for reviewing. Command directly from the main menu. WYSIWYG report generating. Selective event reporting. Supports MAG and Wiegand signaling. Filtering from the events table.
Add to Compare
Enables granting access to CyberLocks based upon the values of user-defined fields in People, Lock, People tag, and Lock tag records Unlike the traditional static tags, locks and people are automatically added to and removed from Dynamic Tags based upon whether their user-defined field values match the criteria of the tag Can automatically grant or revoke access when the attributes of a person or lock change
Add to Compare
Includes three security features - The first is an option that makes the first key of a multi-key operation the sole key able to open a CyberLock within a sixteen-second window. The second adds a Temporary Activation option that enables activating an expired CyberKey for five minutes by touching a selected CyberLock or CyberPoint® on legacy CyberKeys G2. A CyberKey can support temporary activation times between 2 min and 72 hours. The third feature provides an option to limit temporary activation and one-time use settings on legacy CyberKeys to an eight-second window.
Add to Compare
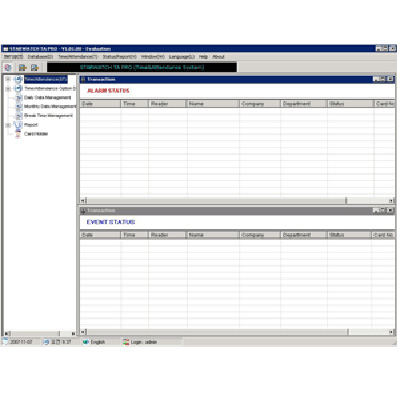
webEntry™ TimeManager is a reporting method for the office manager/administrator who requires statistics on the in and out movements of staff. Using transaction files, automatically emailed from the webEntry™ controller, the software provides a configurable tool that allows the administrator to run reports on the number of hours worked by staff. Rather than installing a separate timekeeping system, existing pass cards and readers can be used for both access control and time and attendance reporting.
Add to Compare
Adds features required to manage all the functionality the door & I/O hardware module brings to a Flex System installation In addition to managing individual access rights to each other, Request-to-Exit (RTE) events are recorded, doors can be set to automatically unlock and relock at specified times, doors sensors are monitored, and alarms can be triggered if a door is forced or left open after a specified amount of time
Add to Compare
Adds complete support for adding FlashLocks and fobs to a CyberLock system To grant access, FlashLocks may be added to an access list Fobs may be assigned to people and given an expiration rule Flash access may be distributed by email or text message
Add to Compare
Automates the process of changing lock access codes for some or all CyberLock cylinders in a system Access codes may be configured to change (roll) on a periodic basis A “grace period” may be designated during which the lock will continue to honor the old access codes to complete the change for all affected locks
Add to Compare
For small- or medium-sized companies that need to increase key control and accountability throughout their organisation Manage as many as 500 locks and 500 keys Download detailed audit trails of lock and key activity Set key access schedules (i.e. M-F 8:00 a.m. – 5:00 p.m.) Expire and/or deactivate keys Manage lost keys Program locks with a multiple key mode (requires more than one key to open a lock) Program locks with a delay mode (a period of time before the lock actually opens after a key has been presented) Configure automatic email notifications on access activity (i.e. low battery, key expiration, notification of events) Grouping capabilities for locks and people Access through a LAN or securely over the Internet
Add to Compare
CEM AC2000 Guard Tours provides the facility to define a list of readers/ inputs that a security guard must visit in a certain order and within a specified time period. If the guard does not either swipe at a pre configured card reader time or activate a pre configured input within the guard tours parameters, an alarm will be sent to the AC2000 AED (Alarm Event Display) application.
Add to Compare
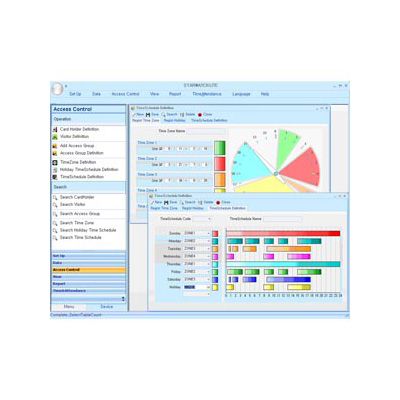
Display: 65,536 Color(16bit color) viewed at 1024 x 768 resolution. Drive (CD-ROM): Over 8 Double Speed Drive Recommended. The STARWATCH ENTERPRISE is dedicated access control software with various unparalleled features. This versatile software allows management of multiple sites, zones and companies as well as integration with video surveilance systems.
Add to Compare
An access control system for stand-alone application or for integration with other systems, such as the Bosch video management system BVMS or Bosch B and G series intrusion panels As a stand-alone system, it features a simple-to-use map and alarm viewer for a rapid assessment of all the devices and entrances on the site As an integrated system, it allows the operator of a video management system to perform door-related tasks like video-based ID verification, to grant and deny access, or to disable doors Intrusion areas can be armed directly from the Map View, and intrusion panel users can be centrally managed Combines high-end access control features, performance and availability with intuitive operation Web-based visitor management Comprehensive security management: Integrates with intrusion and video systems Highly scalable Easy to configure
Add to Compare
An access control system for stand-alone application or for integration with other systems, such as the Bosch video management system BVMS or Bosch B and G series intrusion panels As a stand-alone system, it features a simple-to-use map and alarm viewer for a rapid assessment of all the devices and entrances on the site As an integrated system, it allows the operator of a video management system to perform door-related tasks like video-based ID verification, to grant and deny access, or to disable doors Intrusion areas can be armed directly from the Map View, and intrusion panel users can be centrally managed Combines high-end access control features, performance and availability with intuitive operation Web-based visitor management Comprehensive security management: Integrates with intrusion and video systems Highly scalable Easy to configure
Add to Compare
Idesco ID lets you easily and cost-effectively integrate mobile identification into your own conventional access control system. It does this first by eliminating any need for a parallel stand-alone system or registering with a cloud service. This greatly simplifies management and distribution of users’ mobile credentials because Idesco ID lets you send them directly from within your own system. Idesco ID also provides its own user-friendly mobile app to users free, letting them conveniently enter your site’s doors using only their mobile phones. Large organizations choose from two integration options for Idesco ID. Either initiate mobile credential registration with all your organization’s phones at one time or integrate Idesco ID to initiate credential registration whenever a new one is needed, 24/7/365. Small organizations with only intermittent need enjoy an even simpler solution. When your user downloads and installs free Idesco ID mobile app, it automatically embeds a unique mobile credential in their phones. Idesco’s pc-connectable Enrollment station will detect and forward this credential directly to your system. Idesco ID app connects with Idesco’s mobile-compatible 8 CD 2.0 MI readers. Idesco ID won’t require any cloud service. Alternatively, you can opt to integrate your own existing mobile access app to Idesco ID service. This lets you register mobile access for users’ phones – again, directly from your own system. System managers choose from three different security levels for each reader; 1) convenient and hygienic hands-free access without touching the phone, 2) choose nearby door from phone’s screen, or 3) first release phone’s own security lock before choosing door.
Add to Compare