Access Control Softwares (653)

Reduces IT certification requirements/costs Cellular/Ethernet communication option removes hardware installed on your network Eliminates one-time and annual costs of maintaining servers, network and database admins Supports rapid deployment of software and firmware updates AES 256 Encrypted Communication complies with Federal Banking Regulation requirements on data storage and communication
Add to Compare
CEM AC2000 WEB Room Booking system allows users to define and book meeting rooms for a configurable period of time. The AC2000 WEB Room Booking function can be used in conjunction with the emerald™ TS300 touch screen terminal, which now includes Room Booking Remote Applications.
Add to Compare
Extend BIS Access Engine by the ability to control and manage doors that are not continuously online. Enjoy the advantages of centralised door management without the cost of a dedicated network. Choose from a wide range of compatible lock cylinders and door fittings.
Add to Compare
CyberLock SP-100 is a cyberaudit server is an excellent choice for small- or medium-sized companies that need to increase key control and accountability throughout their organisation. It offers the basics of access control—scheduled access, auditing, and reporting—plus offers many advanced features such as email notification of events, key expirations, lost key blocking, and multiple key & delayed access.
Add to Compare
Enterprise Access 2000 is a windows based software package which is used with ACT control units to provide a networked access control system for up to 8 doors. The user friendly software uses the familiar windows style of data entry for all the access data such as user details and programming of the door control units. When all the information has been entered it is downloaded and stored in non volatile memory at each control unit. Where systems are networked together the download of data can be achieved via the network or by downloading the data into each individual control unit using a laptop computer. The advantage of holding the information at each control unit means that it is possible for the access control system to function offline without the PC connected. When the PC is connected and the system is online it is then possible to retrieve the activity logs from the control units and obtain screen reports and printed reports.
Add to Compare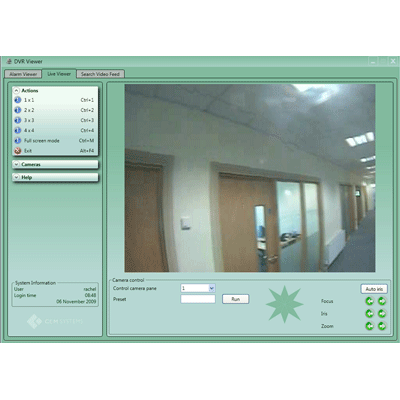
The AC2000 DVR suite of applications provides the ability to associate access control alarms with digital video clips. The DVR Configuration Module seamlessly integrates AC2000SE with Digital Video Management Systems (DVMS) giving the operator a range of video imaging facilities to generate alarm reports with associated video, view live video feed, control camera positioning, control image quality and capture images to file.
Add to Compare
SkimGard® technology is engineered to constantly monitor a defined area in front of the reader surface. The reader faceplate contains raised sections which provide for a mechanically difficult area to install a skimming device. When an object is placed over the card slot (for a pre programmed time interval), an input will be activated on an existing alarm system
Add to Compare
Access management can be based on individual competencies allowing business to effectively manage compliance with business policy and government regulations. Access management can be based on individual competencies such as: Safety - is the employee inducted, trained, licensed and fit for work?Equipment - does the employee have the right vehicles or safety equipment?Security - does the employee have the right clearance?Regulatory compliance - are there other requirements the employee has to meet?The platform can also take account of validity periods and competence expiry. Access decisions are delivered to the individual instantly by the door reader or display monitor or via SMS.
Add to Compare
Gallagher's Prepay Car Parking feature allows you to bring the revenue from your site's car parking facilities directly back to your business. Third party car parking vendors often take a large portion of each transaction as a fee, but with Gallagher's solution, you don't miss out. Staff, students, contractors, or frequent visitors can all use their existing access cards to gain entry to a car park, and their credit total within Command Centre is automatically adjusted to reflect their purchase for the week/day/hour. Additionally, via Gallagher's Cardholder REST API a website can be built to allow cardholders to purchase their credits and check their balances online from anywhere. Their account within Command Centre will then be updated to reflect the purchase. Users can also be notified that their accounts are getting low via emails or SMS messaging.
Add to Compare
Symmetry Business Intelligence delivers critical information through data analysis to help identify the employees, contractors and other identities that may pose the highest risk to the organization. Each person’s access history and patterns are analyzed and a risk score is assigned and updated over time. Anomalous behavior is flagged, helping identify potential threats, better control access and prevent data theft. Identifying potentially risky behavior, allows earlier detection of potential threats, thereby mitigating risk and reducing the potential cost of an incident. Dynamic - Dashboards provide a real-time visual representation of the movement and trends of people. See a summary of the identities with the highest risk scores as well as more detailed activity each hour of the week. Risk Score - Risk scores provide early insight into potential risks when a score rises. Scores are generated based on the reader location, time of day and a user’s access patterns. Operate Efficiently - Critical alarms are flagged saving time and prioritizing identities with anomalous behavior. Use Existing Data - The cloud-based system integrates with and collects data from Symmetry Access Control and Symmetry CONNECT Identity Management to evaluate the risk landscape. Policy-Driven - Define risky areas and times to determine the weight of each behavior towards the overall risk score. Make Informed Decisions - Evaluate an employee or contractor’s risk score and past activity to determine if access should be granted to sensitive areas.
Add to Compare
Send secure, targeted alerts and updates to specific groups in real-time. Communicate quickly and accurately to all cardholders during emergencies. Ensure authenticity and trust with customised templates, and the Mobile Connect App. Configure both static and dynamic recipient groups. Save time and reduce the risk of human error with automated Broadcast Notifications. Immediately identify and report on successful or failed to send notifications
Add to Compare
Gallagher Challenge provides an additional tier of security for businesses or areas where a higher level of security is required. Gallagher Challenge enables an operator to double-check cardholders’ identities as they pass through a door by providing a visual comparison of the cardholder’s image from their record and their live image or one provided via video. Features include: Fully integrated with video systemsAn inbuilt screen designer allowing sites to select the specific information displayed to the Challenge operatorAllows flexible queue management of Challenge events across single or multiple workstations
Add to Compare
Gallagher’s solution allows sites to monitor the time cardholders are spending within designated areas, create alarms, deliver notifications, and to automatically record events for reporting. Features include: Alarms when a cardholder is in a zone too long Alarms when a cardholder has not spent enough time offsite Alarms when a cardholder has spent too long onsite cumulatively (weeks or months) Immediate notifications to supervisors (text message or email) for instant action Automatic access control (access privilege removed at the end of a shift) An audit trail for reporting.
Add to Compare
The Gallagher video interface provides the ability to connect to third party systems providing integration of key operations for video and alarms management. An integrated video solution links visual records to events in Gallagher Command Centre. Recalling a specific event allows associated stored video images to be immediately retrieved. Live video can be fully integrated with site monitoring screen layouts enabling configurable, localized monitoring and control panels to include cameras, site plans, status, guard tours and filtered event trails.
Add to CompareThe Cardholder Change Tracking API enables a third party application to retrieve properties from the Gallagher Command Centre database. The query polls the Command Centre database and, if a change has occurred to a cardholder's properties since the previous poll, the query will retrieve the cardholder's current properties. This API is used when Command Centre is the source of truth. Your HR or IT system will be updated to reflect the changes made in Command Centre. Updates include changes to a cardholder's personal details, card assignments or access group assignments.
Add to Compare
Data Security, easy configuration & language translations is access control software that offers industry-leading data protection between the Gallagher Command Centre and Controllers, using up to 256-bit AES encryption. It is easy to install, user-friendly and intuitive.
Add to Compare
IP-based encrypted network communications between Command Centre and Controllers ensure your data is secure. Distributed intelligence and data storage allow for continued operation of access control and alarms management in the event of a network communication failure on site. Gallagher Controllers are capable of buffering events which are then automatically sent to Command Centre when communications are re-established.
Add to Compare






