Access Control Softwares (653)

Infineon’s SICRYPT CSP (Crypto Service Provider) implemented on Infineon’s chipcard- and security controller supports the security token enabled Windows 2000/XP Public Key Infrastructure (PKI). It can be implemented on smartcards as well as in USB-Tokens. Features client identification, public key interactive logon, and email-enabled.
Add to Compare
Q-ie was designed to support the Syclon panel current loop architecture, which can support up to 56 26-bit Wiegand readers. The software consist of 5 components namely Q-ie Server or CSRD (Central Services Redirector), Q-ie Workstation, HDC Controller, Q-ie Web based, Report Server and Database. The function of the Q-ie server is to store the configuration in the database, to send events to workstations and log them in the database and to communicate with the HDC Controllers and update them with the latest configuration changes.
Add to Compare
TagTrac’s system architecture is a multi-tiered multi-threaded distributed network designed for use over LAN/WAN/GAN to manage buildings, their assets and their staff. The Database Server (DBS) provides the system with rules to follow and information on which to act. The Floor Server (FS) is the systems real-world interface, and will connect to the DBS via TCP/IP ensuring a truly distributed architecture. Floor Servers will integrate into real-world devices such as Readers/ReaderNets, Biometrics, Digital I/O devices, real time video etc. giving the system the ability to monitor, verify and control access as well as building functions such as geysers, lights, etc. The Console (CS) is a monitoring station for the system. Also TCP/IP based one could conceivably dial into the system from home and perform actions as well as draw reports and monitor system activity.
Add to Compare
ApolloVision delivers a total security solution by combining quality video monitoring, high capacity storage with great scalability and ease of use. ApolloVision empowers Apollo Access Control Systems with the force of a fully integrated digital video system.
Add to Compare
OnSite Aparato is a full-featured appliance-based access control platform with unmatched built-in security features. With a capacity of up to 1,000 readers and half a million active card holders, Aparato’s scalable licensing model gives users the ability to choose the system that best fits their needs, increase capacity as needs grow, and add capabilities in an à la carte manner.
Add to Compare
TITAN is a true 32-bit access control application that provides Windows interface for management, control and monitoring of the entire Challenger range of products. These include access control, alarm monitoring, HVAC, lighting control as well as video imaging system. Some of the other features of the system are: full upload and download capabilities; alarm handling, monitoring and control via graphics maps; Smart Card programmer facilities for the creation, programming and loading of Tecom Smart Cards and Readers; Alarm handling through a 2 tier response process with individual programmable instructions; flexible database and history reporting schedule and support of multiple card reader technologies.
Add to Compare
APPLICATIONS & BENEFITS Access Control Visibility Data visualization capability with intuitive user-friendly interface Event tracking of door activity and active users with alert settings and reporting features Event classification to organize activity by critical action required Device status read-out in access control solution User and credential management as well as group access permission management Lockdown feature to secure the facility in an emergency Live and recorded video capture and indexing Flexibility and Control Mobile credentials to modernize workforce and facility Remote and mobile management to control from any device and from anywhere Role-based permissions Event and user access automation and scheduling Automated user access privileges and ability to schedule events Identity Access Management to tie user physical security access rights to online access Infinite scalability to grow Site and door management to set up building access perimeter and interior doors Data Analytics and Insight Data Explorer business intelligence tool built into the platform for advanced analytics Global View map-centric multi-site display to zoom into individual facilities to assess usage patterns and risks Hundreds of API integrations to expand connectivity and develop ecosystem Event trend analysis automatically identifies patterns and anomalies in the access data to surface potential issues and confirm if the event is normal or anomalous
Add to Compare
Cognitec Systems, the leading provider of face recognition technology and systems, announced that the company had been awarded a contract to provide software and services to the German Federal Criminal Police Office (Bundeskriminalamt - BKA) after winning a pan-European tender.On the basis of photographs and video material, Cognitec's face recognition software will support the research and identification of unknown suspects. This kind of procedure will mainly be used when identification attempts using fingerprint or DNA have failed or are unsuitable. Research in a central, digital photo archive to identify a criminal will help in cases where only a photograph of an unknown suspected person exists. The Federal Criminal Police Office will use Cognitec's software and respectively such type of research in a number of occasions, such as the tracing down of persons who, in the cause of the investigation, appear suspicious by using fake personal documents or payment cards or, for instance being involved in bank robberies. It will also be used for the identification of missing and helpless persons.Alfredo Herrera, Managing Director of Cognitec Systems GmbH said: "We are delighted that Cognitec was chosen for this important project by the Federal Criminal Police Office and that we are given the chance to provide them with our latest facial recognition technology. Cognitec is convinced that our system works on the highest level when it comes to speed and reliability and will turn out to be an indispensable tool for the daily work of the Federal Criminal Police Office."
Add to Compare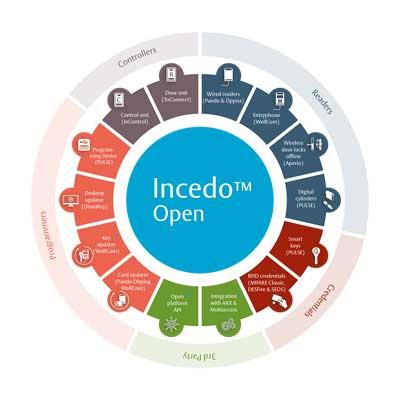
A flexible cloud-based modular platform Allows to combine offline and online solutions, digital lock systems and entry phone in a cloud-based access control system Offers digital planning and digital management of access control systems Through digital locks, cylinders and a smart entry phone, Incedo™ Open facilitates efficient key management Cloud-based access control system No in-house server required Easy to expand Easy to upgrade Graphic planning and management Enter properties in interactive Google Map Import property drawings Place readers, entry phones and digital cylinders via interactive property drawing Monitor system status and receive clear indicators if anything is wrong Functions for apartment buildings and for small and medium-sized businesses Manage contracts and apartment information for apartment buildings Manage control of external alarm systems for small and medium-sized businesses
Add to Compare
The LEGIC biometric™ Standard is based on an open LEGIC data structure (LEGIC biometric segment) and standardises the biometric verification (1:1 matching) of persons for access and time & attendance in organisations. It ensures the compatibility of biometric applications between different license partners and increases the multi-application capability in projects that use the LEGIC technology.
Add to Compare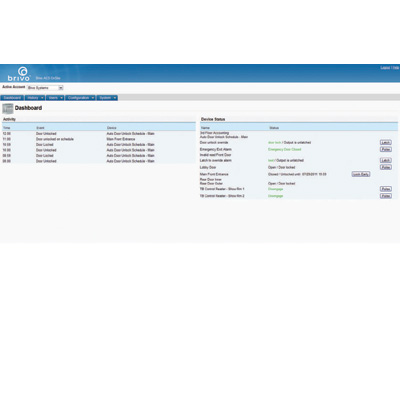
ACS OnSite is a cost-effective, easy to use, Web-based access control solution that requires no dedicated PCs and provides robust access control features. ACS OnSite is ideally suited for providing security at a single facility, even if that facility houses more than one business. The system is also fully convertible to accommodate the growth of a business to additional facilities.
Add to Compare
There are many challenges facing businesses of every type and scale, these include hybrid working, efficient use of multiple rooms and reducing energy consumption. Security that is agile and futureproof helps to address them. These challenges are greatest for small or medium sized organisations where flexibility is key. ASSA ABLOY are able to offer a huge, diverse range of door hardware, all from one manufacturer, commissioning or extending control becomes more streamlined and cost-efficient. Flexible control for security, agility and efficiency A modern access control solution should offer a wide range of digital locks and credentials, allowing a business to manage their workspaces and workflows with maximum efficiency. ASSA ABLOY’s Incedo access control solutions were designed for this purpose, with the option to upgrade to the Cloud. When they choose Incedo, organizations secure almost any opening with offline electronic locks or in real time with online devices. They issue building users with credentials of their choice. And they manage everything from one place, via the flexible, scalable, intuitive Incedo platform. It is easy to get started with Incedo. Businesses choose from a vast range of hardware. Doors, cabinets, gates, server racks and almost any other opening may be locked with a wireless or wired device. Building users gain access via smartcards, mobile keys stored on their smartphone, or battery-free smart keys. Our range of credentials can be used across our vast hardware choices. Incedo software manages this hardware and the security of users — in the cloud, if required. Hardware and software installations are easy, with no complex integrations required. The entire ecosystem is modular, designed for simple adoption and easy expansion at any time and in any direction. Incedo leaves business owners with more time to focus on their main task: the business.
Add to Compare
Supports changes of facial expression and presence of glasses, beard, scarves, or hats Ability to register people based on one or various photos and videos Integration with third-party access control systems Exportable alarms to PDF and Excel format Integration API available
Add to Compare
Another large survey confirms the growing importance of integration across building security functions. According to the Wireless Access Control Report 2021, “95% [of security professionals] cited system integration [of access control] with other building/security management functions to be ‘somewhat’ or ‘very’ important” for the coming five years. Extensive expertise in the security sector made Plexus’ procurement team aware of this growing need for connectivity across functions — including access control. Plexus managers sought a more flexible access system for their own head office in Swansea, Wales. Alongside integrated control, Plexus prioritized modern access control with lower maintenance costs than their current system, as well as the potential to be operated securely from the cloud. Any new installation should offer the option to further scale — in any direction — in the future. They require a broad choice of wireless and wired door devices and readers for multiple types of opening — and of course a straightforward upgrade path for both hardware and software. ASSA ABLOY Opening Solutions’ Incedo™ Business platform is now running at Plexus. Installing wireless locks, readers and controllers from the broad ASSA ABLOY range was fast and simple, streamlining their switch to Incedo Business. “Hardware architecture is well manufactured, and this goes hand-in-hand with software that has fantastic ease of use,” says Marcus Elphick, Operations Director at Plexus Fire and Security. Coming soon: fully featured cloud management With keyless locking and Incedo Business management software, Plexus managers control exactly who goes where around their offices. They can set times when defined user groups may open specific doors. It keeps staff moving and safe without the hassle of physical keys. The “new software has been seamless, much simpler and [with a] common sense approach to structure,” says Marcus Elphick. Incedo Business software is intuitive to operate from any PC. The entire Incedo platform is fully flexible and modular, allowing Plexus to add more locks or change management software options whenever they need. They are already planning to extend control: remote sites, entrance gates and warehouse access control will be covered, too. “We have been so pleased with the system and its capabilities,” he adds. Plexus aim to quickly upgrade to new Incedo Business Cloud management, which offers them real-time 24/7 access from anywhere, and for a greater number of doors, as they look to expand coverage to more sites. “Incedo’s integrated access control platform already delivers connectivity and convenience,” says Stephanie Ordan, VP Digital and Access Solutions at ASSA ABLOY Opening Solutions EMEA. “Now it delivers in the cloud, too. Incedo keeps premises secure and filters access intelligently, to manage the ever-changing movement of people — from anywhere.” “Your business is not static, and there is no reason why your security should be.” “Incedo’s system management options scale from entry level up to cloud-based administration,” adds Kevin Hoare, Incedo Product Unit Director at ASSA ABLOY Opening Solutions EMEA. “You can manage multiple sites and third-party integrations, including security solutions like CCTV. Scale up and down, add or remove hardware and credentials on demand — or switch system management options — all within your single environment. Migration between local and cloud management is always seamless in any direction, ensuring total flexibility for your business.” Whatever the 2020s bring next, Incedo gives security the flexibility to adapt.
Add to Compare
ENGAGE cloud-based web and mobile applications are ideal for basic access control within small businesses and multifamily properties. Connect compatible devices over Wi-Fi for periodic updates or use No-Tour which enables Schlage smart and mobile credentials to deliver updates to devices. ENGAGE for access control supports Schlage Control®, NDE, LE, and CTE with MTB readers as well as Von Duprin RU and RM.
Add to Compare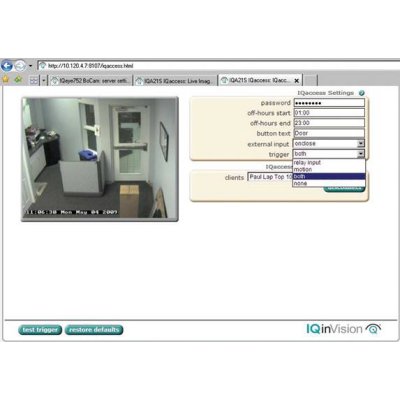
Whenever IQaccess is triggered, a video alert window pops up in every IQaccess enabled PC and lets the first responder open the door, activate the alarm, turn on the lights or control any other device you may have connected to your IQeye PRO LINE camera's relay output.IQaccess features: Field upgradeableUp to 8 local or remote usersFree downloadable client software"After Hours" schedulingPassword protectedTriggered by External Device or On-camera Motion DetectionLow-processing requirementWorks seamlessly with NVRs and IQrecorder Easy installation IQaccess is simple to install and operate - simply upgrade your IQeye PRO LINE camera, install the client software, register the cameras and you are done! You can even have IQaccess trigger your home PC. Most popular applicationsIQaccess is perfect as a notification tool to alert the staff when a client or customer is waiting or is somewhere they shouldn't be. It's also a perfect tool for verifying who is at the door before letting them in. Key applications include:Retail shops Healthcare facilities and campusesHotel front desk areaCorporate officesEducational facilitiesIQaccess is available with the following IQeye PRO LINE cameras:IQeye Sentinel™ SeriesThe first all-weather, megapixel IP network camera that is entirely Power-over-Ethernet. This vandal and tamper-resistant surveillance camera features easy installation with flexible mounting options for wall, ceiling, or parapet.Features:IP 66 / NEMA 5 environmental rating-22°F/-30°C to +122°F/50°C1.3 Megapixels @ 30 fps2.0 Megapixels @ 20 fps3.1 Megapixels @ 12 fps5.0 Megapixels @ 10 fps64 independent video streams with IQcameo<0.05 Lux IR sensitive (Day/Night series)Multistream low BW + Hi ResolutionIEEE 802.3af ~ Power-over-Ethernet360° + Pan, 180° + TiltDigital image cropping for bandwidth optimizationIQeye Alliance™ SeriesThe first fully integrated, Power-over-Ethernet megapixel dome camera line that features solid construction, convenient installation features like a unique pivoting shroud and high-quality video images and network performance.Features:Vandal-resistant, low profile surface mount housingInterior or exterior security video solutionOptional H.264 with audioFull 3-axis gimbal with pivoting, hinged lens shroud64 independent video streams with IQcameoAnalog video out for installation / set-upExtra analogue video for public view monitorSDHC card slot for on-camera storageVGA resolution @ 30 fps1.3 Megapixels @ 15 fps 2.0 Megapixels @ 15 fps3.1 Megapixels @ 12 fps5.0 Megapixels @ 10 fpsLIGHTGRABBER II low-light featureIEEE 802.3af - Power-over-EthernetLow 2.5 watts power consumptionPrivacy zones, digital image croppingAdjustable exclusion zones for harsh lighting conditionIQeye700/750 SeriesThese full-featured megapixel network cameras deliver best-in-class image quality, dynamic range, and exceptional low-light and day-night performance with network stability you can rely on in the most challenging environments.Features:1.3 Megapixels @ up to 30 fps2.0 Megapixels @ up to 20 fps3.1 Megapixels @ up to 12 fps5.0 Megapixels @ up to 10 fps64 independent video streams with IQcameo<0.05 Lux IR sensitive (750 Series)MultiStream low BW + Hi Resolution IEEE 802.3af - Power-over-EthernetPublic View Port™ Analogue outputCF slot for on-camera recordingLIGHTGRABBER II™ low-light feature
Add to Compare
Works with range of readers and wireless locking devices, providing secure, convenient access for building users Users unlock doors and other openings with a smart device instead of traditional hard credentials like RFID cards and tokens Operates award-winning Seos® credential technology for powerful encryption, identity management and data protection Convenience: there is no need for a separate RFID credential when you open secure doors and openings with a device you already carry Flexibility: facility managers amend, issue or cancel credentials from anywhere; building users always have their access rights up to date Security: users notice a missing smart device more quickly than an RFID card or token, and on-device passwords and biometrics keep thieves out Efficiency: employees waste less time collecting or amending access credentials in person; visitors get instant temporary access when they need it Connectivity: maintain an “always-on” link between your Incedo platform and its users, enabling access permission changes in real time
Add to Compare
Real time monitoring, customizable dashboards and live alerts Full reporting suite Web API Fully hosted access control platform Custom rules engine Partitioned tenants with defined areas Predefined and customizable user roles and permissions
Add to Compare
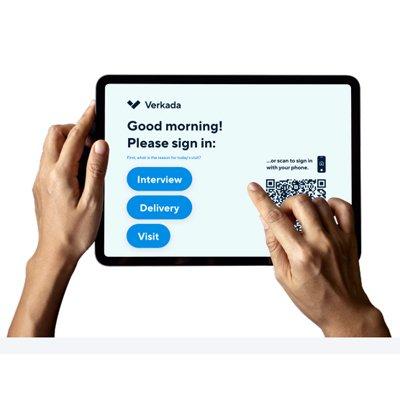
10-year Guest visitor management system licence Centralised guest management across all locations Verkada Access Control integration Verkada Camera integration Guest tracking within Command platform Remote door unlock Unlimited users, visitors and sign-ins Touchless sign–in Self sign-out Custom branding Document signing Instant host notifications Photo capture Badge printing Detailed guest logs Role–based permissions and settings Site–specific host lists Centralised dashboard Real–time analytics Exportable reports Dedicated support
Add to Compare
The LEGIC access™ Standard is based on an open LEGIC data structure (LEGIC access segment) and standardises person identification for access and time & attendance in companies. It ensures the compatibility of access and time & attendance applications between different license partners. Additionally, it increases the multi-application capability of the respective projects using LEGIC technology.
Add to Compare
1-year Guest visitor management system licence Centralised guest management across all locations Verkada Access Control integration Verkada Camera integration Guest tracking within Command platform Remote door unlock Unlimited users, visitors and sign-ins Touchless sign–in Self sign-out Custom branding Document signing Instant host notifications Photo capture Badge printing Detailed guest logs Role–based permissions and settings Site–specific host lists Centralised dashboard Real–time analytics Exportable reports Dedicated support
Add to Compare
Verkada Command offers a web browser-based interface for designated users to monitor live feeds, receive calls, and respond with one-tap controls from virtually anywhere, any device. Receivers can also field numerous concurrent calls in Command: they can easily view all incoming calls, see how long the caller has been waiting, and know if anyone else has responded to the call. With this information, receivers can prioritize which calls to answer and which calls to place on hold.
Add to Compare
Powered by Bluetooth Low Energy (BLE), Verkada Pass is a mobile app that allows designated users to receive intercom calls and respond on the go, even if they are away from an entryway or computer. Designated users can access the app on both iOS and Android devices and easily use one-tap controls to admit visitors. Outside of call receiving, employees in proximity of the intercom’s built-in card reader can also use the app to unlock doors and enter buildings.
Add to Compare
5-year Guest visitor management system licence Centralised guest management across all locations Verkada Access Control integration Verkada Camera integration Guest tracking within Command platform Remote door unlock Unlimited users, visitors and sign-ins Touchless sign–in Self sign-out Custom branding Document signing Instant host notifications Photo capture Badge printing Detailed guest logs Role–based permissions and settings Site–specific host lists Centralised dashboard Real–time analytics Exportable reports Dedicated support
Add to Compare