Access Control Softwares (653)

Verkada Desk Station is an iPad-based application that allows receptionists, guards, and other stationed professionals to monitor live feeds, and easily respond to calls with one tap. Organizations can pair an unlimited number of intercoms to their tablet and view up to four intercoms or neighboring cameras at once. Receivers can also step away from their station with a “Here/Away” button that will program calls to automatically skip the Desk Station when toggled and ring whoever is next in the call flow.
Add to Compare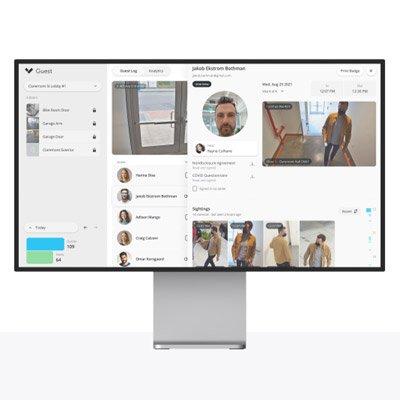
3-year Guest visitor management system licence Centralised guest management across all locations Verkada Access Control integration Verkada Camera integration Guest tracking within Command platform Remote door unlock Unlimited users, visitors and sign-ins Touchless sign–in Self sign-out Custom branding Document signing Instant host notifications Photo capture Badge printing Detailed guest logs Role–based permissions and settings Site–specific host lists Centralised dashboard Real–time analytics Exportable reports Dedicated support
Add to Compare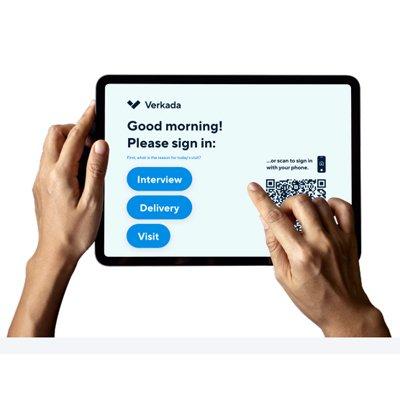
Integrate with Verkada Cameras & Access Control Role-based permissions Customizable visitor experience Touchless check-in Calendar invitations Document signing Badge printing Automatic arrival notifications Analytics and reporting Security Screening
Add to Compare
Brivo Systems LLC, leader in cloud applications for security management, recently announced the company’s release of Brivo OnAirSM version 10.11, featuring an updated User Interface (UI). Brivo OnAir is the new brand name for the former Brivo ACS WebService cloud-based access control management solution. With the introduction of this updated interface, Brivo further extends its leadership in the cloud-based access control and video surveillance space by offering a more visually rich and responsive experience for its customers. The Brivo OnAir interface is streamlined and designed for usability, reducing the learning curve and simplifying both system deployment and day-to-day security management. For the redesign project, Brivo engaged a team of user experience (UX) experts. The team conducted hundreds of hours of interviews with current and prospective users to determine how they worked. They incorporated this information into profiles of user “personas” in order to bring focus to ensuring that the resulting interface responded to the needs of Brivo’s users. This first phase of the interface re-design incorporates the key findings from this process and sets the stage for additional enhancements to follow. “This is an exciting day for Brivo, our channel partners and end-users,” said John Szczygiel, Executive Vice President. “The Brivo OnAir name better captures the essence of our cloud-based solution. The revamped UI directly reflects feedback from our users and further demonstrates our commitment to continuous improvement. What's more, this major upgrade is delivered automatically and without charge to all of our users. That’s cloud computing, that’s Brivo OnAir.” Among the features the Brivo OnAir version 10.11 offers: A rich user experience that maximises video and access control management. A new top-level video tab provides immediate access to recorded and live Online Video Recorder (OVR) video. Simplified search capability provides a comprehensive view of access and video motion events on a timeline display; events are visually represented and prioritised using color coding, intuitive icons and other visual cues. The system landing page is optimised to provide shortcuts for everyday operations: create a new user, find a user or a card, change passwords and search video all on this page—saving time navigating through multiple screens.
Add to Compare
OVR WebService significantly extends Brivo’s ACS WebService, providing centralized video storage alongside hosted access control. View live or event-related video at a fraction of the cost of traditional hardware DVRs. OVR WebService is available to all of Brivo’s ACS WebService customers.
Add to Compare
Group 4 Technology, an advanced security technology solution developer with over 15,000 installations in 60 countries, releases its new multiMAX version 5.0 access control and security management software. The new version 5.0 software features an expansive set of new and improved capabilities, such as an enhanced visitor management system and expanded digital video recording (DVR) integration options.The new version 5.0 software improves on Group 4 Technology’s already easy-to-use interface with new graphical calendars, system-wide time code visualizations, and real-time, on-screen alarm statistics.Version 5 offers a new optional upgrade module, Threat Level ManagerTM. This module enables one-touch total system reconfiguration. Five fully customizable security configurations range from green (low) to red (high). Threat Level Manager prevents inconvenience during low threat times, and keeps staff on alert during high threat periods. Threat Level Manager is perfect for holidays when users want to make many configuration changes.Version 5 revised and improved the Visitor Management System. Users can pre-enroll visitors to save time and populate up to 50 fields of visitor data. The visitor management system can operate as a standard client or as a web client using existing Intranet/Internet Communications. Define visitor’s access level, capture photos and print visitor badges. Assign visitors to authorized employees if you choose the option to make visitor assignments mandatory.More new features include: Predefined commands allow specific commands to be created and added to maps for use by security guards and others with limited system access rights. Transaction processing system replaced with Microsoft Message Queue to improve performance of 5000 plus card reader systems. Real time alarm filter and on-screen alarm statistics provide immediate data to make instant decisions. Link cardholder record to the alarms and current activity screens.
Add to Compare
CA3000 SQL is a true 32 bit, multi-tier application that runs on Windows 2000, Windows 2000 Pro and Windows NT. Clients operate on Windows XP, 98SE, NT or 2000. The CA3000 successfully integrates advanced client/server system architecture, scalable MSDE/MS-SQL database technology and advanced networking capabilities to provide an easy to program and easy to use integrated access control and facilities management system. The integration of CCTV control with pan, tilt and zoom capabilities and comprehensive alarm processing provides secure environment. Flexible database partitioning facilitates segmentation of the database into "sphere of control". Supports Continental's full line of intelligent controllers and comprehensive reader technologies like Proximity, Weigand, Keypads, Magnetic Stripe, Barcode and Biometrics.
Add to Compare
Configuration and management of integrated security systems often is complex and time consuming because of project size, number of security applications involved and the interaction between them. Easy configuration and management tools have become vital.The Belgian manufacturer IDCS, with 18 years of experience in Integrated Security Solutions and references in the most prestigious buildings in Europe, provides with its newest Management Software INVISE for its S2000 Integrated Security System a revolutionary change in easy configuration and management. Highlights: Seamless integration of Access Control, Intruder Detection, Digital Video, Visitor Control, Presence Control and Car Park Control Object oriented design - doors, intruder points, technical points etc are considered as objects. Through simple drag and drop functions and dialogue windows these objects are linked to reader types, video recordings, photo-id checks, alarm verifications, function commands, graphical maps Seamless integration with IP-video and IP-biometric identification: direct links between any event and video data Comprehensive real-time graphical map management Full drag and drop time zone management Server redundancy
Add to Compare
ProTime Attendance Management systems offer the user flexible or defined working hours, rest periods and managed absence. ProTime may be installed as a standalone, single station system or a multistation system on a MS network. The system can accommodate up to 32 terminals. Features Wiegand, proximity and magnetic stripe technologies. Software can be tailored from 50 employees up to 6,000.
Add to Compare
With the SMARTair® Openow™ app, security managers enjoy Update-on-Card functionality and a touchless credential handling process. Openow brings online benefits to existing offline devices in a SMARTair access control system, so management tasks are completed more efficiently. Powerful features usually only available in online mode are now enabled for SMARTair offline locks — without any need to fit dedicated wall updaters or communications HUBs. This means no cabling at all; and faster, less invasive installation. Now, every time a user opens a SMARTair door with Openow, the event and entire door history are reported in the SMARTair software, alerting security managers about low battery status, access denied, out of time zone and more. Openow is the convenient mobile solution for SMARTair wireless access control systems. Users store validated digital keys securely in their own Openow app. To open a SMARTair lock, they simply tap their phone against its inbuilt BLE reader. An encrypted Bluetooth connection connects the phone and locking device to quickly approve or deny a unlock request. With Openow, if you have your phone, you are already carrying your keys. Facility managers get through their access management workload faster when they replace traditional card and tag credentials with Openow. Because Openow and the intuitive SMARTair TS1000 software handle everything, virtual keys may be securely deployed over-the-air to anywhere in the world and security managers can easily and quickly update access plans. Delays in issuing or revoking keys for sensitive doors no longer jeopardize site security or business efficiency. There are no physical credentials to handle or track; no card encoders to buy; and no queues at reception for staff or visitors awaiting credentials being issued. The entire credential handling process — for both building users and security managers — is touchless.
Add to Compare
With CSW-4000, applications and segments are written on a smartcard or another storage medium with an intuitive “Drag & Drop” system. You choose from a clear selection of all available segments and applications and simply drag these segments with the mouse onto the symbol of your identification medium, let it go, and the initialisation is finished. CSW-4000 has a tidy and simple user interface so that you can become familiar with it at once.
Add to Compare
ESi is a complete 32 bit enterprise solution from Public Access Terminals (PAT) that provides you with ID card production, access control, visitor management, reporting and alarm monitoring in a single integrated software solution. Using TCP/IP network protocols eliminates the need to invest in dedicated network cabling. ESi's direct database link means that information need only be entered once, speeding data input and accuracy. Combined with PAT's well established FastNet software, this allows a user to create an ID, encode it as required and issue it to the access control system across an existing network infrastructure, including WAN links, with immediate effect.
Add to Compare
Door Detective creates an infrared field across a doorway to monitor the passage of individuals through the door. It ensures that everyone must present their access card. An alarm alerts security staff of the presence of unauthorised entrants. It detects tailgating, collusion, pass-back and non-entry. Works in conjunction with any access control system.
Add to Compare
The LEGIC cash™ Standard offers a standardised data structure, which allows the choice between various products of the LEGIC cash™ Standard members and ensures their compatibility. Therefore, it is possible to operate products of different manufacturers in the same installation. Additionally, the LEGIC cash™ Standard meets the high security standard of LEGIC’s contactless payment systems and thus can satisfy the requirements of both vendors and operators.
Add to Compare
The biometric facial recognition technology enables one-to-many identification searches and one-to-one verification matches. The technology is most effective as an identification tool capable of distilling large databases down to a smaller gallery of possible matches. The technology consists of a series of components packaged within a Software Development Kit (SDK). These components find faces within a digital photograph or video stream and match those images to like-looking facial images stored within a database. Facial recognition involves three core steps - Create an Encode Array from any facial image, compare a Probe Encode Array to a Stored Encode Array in a database and present results.
Add to Compare
ActiveTrac Software provides enterprise-wide personnel, asset and equipment monitoring solution, with integrated logging, tracking, alert notification, status monitoring and reporting functions. The software combines operator-friendly displays, flexible configuration and instantaneous query functions to offer a powerful tool for tracking movements and automatically controlling remote devices. ActiveTrac has a range of applications, including resource management, asset protection, personnel time and attendance, status monitoring, and inventory logistics. ActiveTrac, coupled with the ActiveTag automatic identification products, offers customers the ability to easily monitor and track asset and personnel movements throughout a facility.
Add to Compare




