Access Control Softwares (653)

With Suprema's CoreStation and readers, you can build a centralized system, which is a system based on access control units (ACU). Suprema's centralized system not only provides the benefits of biometrics, but it also provides enhanced security and excellent system scalability. In addition, the centralized system also enables you to upgrade your existing systems at lower installation cost. Integrated with BioStar 2, this system safely stores all information about each user including the user’s name, ID, PIN, access rights and fingerprint data by storing it on a single device. Suprema's intelligent biometric controller, CoreStation, is capable of performing fingerprint matching as well as RFID cards. It provides differentiated performance and features based on a 4-channel module that boasts superior hardware performance and scalability. Features: Performs 400,000 times of fingerprint matching within 1 second Stores information about up to 500,000 users and RFID cards Stores up to 5,000,000 text logs Controls up to 132 Wiegand devices (DM-20 connection required) Controls up to 64 RS-485 devices Processes fingerprint authentication on up to 8 devices simultaneously within 1 second Outstanding Scalability - You can manage a compartmentalized building such as a research centers or hotel with a single CoreStation. Elevator Control - Grants floor access rights to users and controls the floor buttons in the elevators. High-speed Authentication - Simultaneous authentication on as many as 8 devices can becompleted within 1 second, and up to 400,000 fingerprint matching can be performed per second. Access Control and Time & Attendance Management - Provides a wide range of access control and time & attendance management features and also supports mobile cards.
Add to Compare
The L85 software provides a method to integrate wired and wireless locksets into a DSX Access Control System. The L85 software leverages its Virtual Hardware capabilities to accommodate non-controller based locks and readers. Hundreds or even thousands of these devices can be installed through multiple deployments of the L85 software. Non-controller based locksets are a powerful addition to the DSX Access Control System product line. The L85 software provides powerful flexibility with a fully integrated solution of both hardwired and wireless readers and locks.
Add to CompareVicon VAX-PC-RK is an access control server rack-mount model available in a desktop or rack-mount version (VAX-PC-RK). The Server contains the operating system, database engine, web server, application software and configuration data. The server can be configured with the software license of your choice.
Add to CompareVicon VAX-PC is an access control server desktop model available in a desktop or rack-mount version (VAX-PC-RK). It contains the operating system, database engine, web server, application software and configuration data. The server can be configured with the software license of your choice.
Add to Compare
The Who is In is a Life Safety report that provides a list of Cardholders that are shown to be In a selected area or premise. The inclusion of the cardholder in the report is based on their Zone 1 APB status as being IN for the Location of their last card read. The report can be sorted by Company or by Device location. The report is conveniently initiated from the Who Is In Report Button in the toolbar located at the top of the DataBase program or can be run from the Who is In Report in the reports list. The Who Is In report only displays people whose last card read was within 48 hours of when the report is run. This will exclude people who never read out.
Add to Compare
Man Trap applications are typically two doors in a holding area or vestibule outside of a sensitive room. One door leads to the high security area while the other door leads to the non secured area. The application mandates that the two doors cannot be open or even unlocked at the same time. One door must shut and lock before the other door can unlock and open.
Add to Compare
It is a wire-free system, and each key can be programmed and updated individually to allow access to specific areas at specific times and dates, accommodating constantly changing access requirements and ensuring maximum flexibility. Power is provided by a battery inside the programmable CLIQ® key. The new CLIQ® Web Manager software is built to serve a wide range of workflows. It allows administrators to create individual schedules for users, doors or audit trails. The revalidation function eliminates the risks of lost or stolen keys: a CLIQ® system can be set to require key revalidation when required, making it safe and easy to issue time-limited access to contractors or visitors. In addition, with different user roles, work can be divided between security administration staff. For example, one user role can be defined as “handing out keys at reception”, while another user can be made responsible for changing access rights on cylinders in the field. The CLIQ® Remote Programming Device is invaluable in assisting companies to manage these often complex workflows. Administrators operate the CLIQ® Web Manager over an Intranet or the Internet, using a standard web browser. No software installation is required, which allows for territorial independence and reduces project IT costs. The CLIQ® Web Manager will benefit large companies with complex CLIQ® installations, in particular. Multinationals with multiple administrators for different territories or organisational units can grant all of them simultaneous system access, for example. Granting tailored access to local staff with local knowledge and local responsibilities is straightforward. The software is also available in several languages, ideal for multinationals with a multilingual staff roster. For easy management, ASSA ABLOY offers software as a service hosting, or network-compatible client/server design. And ASSA ABLOY customer service is available around the clock, every day of the year.
Add to Compare
DSX Anti-Passback allows the system to track the in and out status of the card holders. When implemented - if an access code is In, it will only be granted access at an Out device. When an access code is Out, it will only be granted access at an In device. WinDSX provides all three forms of Anti-Passback; Hard, Soft, and Timed. Zoned Anti-Passback is accomplished with four independent zones of Hard (In/Out), and Soft (Entry/Exit) Anti-Passback. Each reader can be in any or all of the four zones. Each card maintains a separate In/Out status for each of the four zones. This allows Anti-Passback to be used on both exterior and interior doors without the two zones affecting each other.
Add to Compare
Image ReCall Display a Card Holders primary Image automatically when their card is used at a predefined reader or manually when the Card Event is clicked on in the Event Monitoring Window of the Workstation program. Devices can be assigned up two time zones to determine when Image Recall is active for that reader. This applies to all Access Granted or Access Denied messages. Manual Image Recall will work even if there are no devices programmed for Auto-Image Recall. Once the Card Holder is clicked upon, their image will display until the next automatic or manual recall of an Image or until the Image is closed and/or until the features is disabled under the Customise Menu.
Add to Compare
Clean Room Annunciation is a simple application that will make a user aware that any two doors are open in an environment where certain doors (could be more than 2) will provide an annunciation or lockout when two doors of concern are opened at the same time.
Add to Compare
With Suprema Mobile Card, use smartphone as a credential to access doors, gates, networks, and more Supports modern mobile communication technologies which are both NFC and BLE. These two technologies enabled at the background and foreground to communicate with the device seamlessly Protects data with ISO 27001 certified system architecture; data encryption in the mobile portal, secure communication between mobile portal and smartphone, store the data in the keychain, mobile credential data validation The innovative system structure works to issue a mobile credential in an instant
Add to Compare
In distributed systems, IP terminal and readers perform the roles of a controller and reader simultaneously. Therefore, you can undertake functions such as user management, access control management, and biometrics with a single terminal. Suprema's IP terminals and readers improve system reliability with easy system configuration and distributed management. It also provides the benefits of simple wiring and low installation/maintenance costs. Features Elevator Control - Grants floor access rights to users and controls the floor buttons in the elevators. Easy System Connectivity & Easy Maintenance - Distributed systems provide easy system connectivity and easy maintenance. Access Control and Time & Attendance Management - Provides a wide range of access control and time & attendance management features and also supports mobile cards. Outstanding Performance & Contactless Authentication - Provides superior performance based on the world's best biometric algorithms and hardware as well as the benefits of contactless authentication via FaceStation 2.
Add to Compare
Handy Safe - BioStar 2 Mobile Card offers tremendous handiness to end-users by storing biometric information to function as a credential in their own smartphones. Compare with RF cards, smartphones are less likely to be stolen or shared. Highly Secured - Securing the privacy of sensitive identity data is more important than ever. BioStar 2 Mobile Card is highly secured as it stores user’s private information only in smartphone besides user’s information in cards are vulnerable to be cloned. BLE and NFC communication - BioStar mobile card supports both BLE and NFC and enables communication method automatically according to a supported communication type(s) from a device.
Add to Compare
WinDSX is a powerful access control and system monitoring application that harnesses the power of the Windows XP, Vista, and 7 Professional™ operating systems. WinDSX combines point monitoring and access control with Photo ID Badging, Time and Attendance, Alarm Graphics, DVR/NVR Integration, Elevator Control, Alarm Email/Text Message Notification, Threat Level Management, HazMat / Emergency Lockdown, and FIPS/TWIC card compatibility.WinDSX can support your access control needs from a single PC or multi-user Local Area Network to an enterprise solution with SQL Server as the database engine. The system utilises TCP/IP network communications to provide user interaction and real time monitoring to the workstation PC's located anywhere on the LAN or WAN. Password protection allows for operator specific capabilities at each workstation.There are two Editions of Software. WinDSX comes standard with a Microsoft Access database engine. WinDSX SQL is designed to work with Microsoft SQL Server as the database engine. Both editions of WinDSX have similar features and capabilities. Microsoft SQL Server is user supplied.WinDSX implements Point and Click operation with hierarchical tree views and pop up menus for ease of use. I/O monitoring and control is achieved through animated icons that depict the real time status of each input or output. I/O points can also be assigned to an Override Group to allow for multiple inputs and outputs to be monitored and controlled from a single icon.Scheduled Overrides can be assigned to individual Inputs and Outputs as well as Override Groups. These schedules allow operators to quickly assign time and date sensitive instructions determining the open/secure status of outputs and the armed state of inputs.
Add to Compare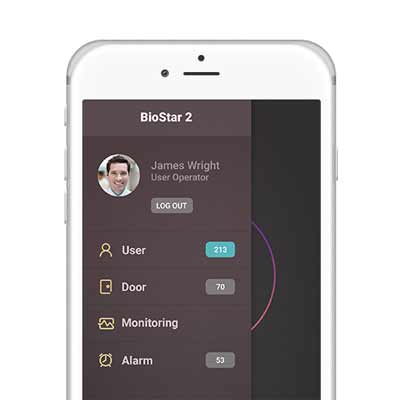
Suprema BioStar 2 Mobile application gives administrators and operators the freedom to manage BioStar 2 anywhere. Administrators can add, edit, or remove users remotely through app. It allows to control door remotely on the mobile device. It can receive live notification and respond to requests or alarms quickly without accessing BioStar 2 via client.
Add to Compare
Administration of Visitors is a seamless feature of the WinDSX System. Visitors can be added to the system and tracked through the secure premises. Reports can be generated showing the Visitors card use and who they came to visit. Just as with most features in WinDSX, Visitor Management can be implemented and deployed in a number of different ways.
Add to Compare
DSX Communications typically run from the Comm Server PC over the customer network to a DSX-LAN module that is connected to the first or Master controller at each Location. Communications then takes the form of a dedicated RS-485 regenerative communications network that runs between system controllers. DSX-IP Gateway changes the way communications are distributed throughout the system.IP Gateway takes the place of a Master controller and will communicate to any Slave or cluster of Slave controllers over the network negating the need for the dedicated RS-485 communications wiring, with the exception of the cabling between controllers in a cluster of slave controllers.DSX-IP Gateway is performed using the standard WinDSX software and the IP Gateway application that is available on all Software distribution CDs. IP Gateway can be deployed on the same PC as the Comm Server or on a separate PC if multiple copies need to be run due to size of system. Each IP Gateway can support 63 DSX controllers or 126 Doors.Scalable Architecture - What you need where you need it.TCP/IP Communications to each Controller or Controller cluster with DSX-LAN Module.Supports AES-256 Communications Encryption to all Controllers without special hardware.Supports 240+ Card and Keypad Formats including FIPS 201 and TWIC.Real Time Processing and Communications between Clusters.Compatible with existing DSX Controllers.Communications to each controller cluster operates simultaneously. These simultaneous communications channels can provide a substantial increase in the rate of data collection and distribution.Each IP Gateway can support 63 DSX controllers or 126 Doors
Add to Compare
Time and Attendance (T&A) is an integral feature of the WinDSX System. WinDSX gathers clock “In” and “Out” times for each user. The operator can then run reports based on the clock “In” and “Out” times of each employee. These reports provide the total number of hours worked per day for each employee and a total number of hours worked for the report period. Reports can be printed or saved to a file.
Add to Compare
BoneID W3 is .NET based platform, on Cloud extension indicates additional modules needed for support from anywhere in the World. In simple words, it is gateway to the Internet. BoneID W3 on Cloud combined with uTouch is amazing solution that comes "out of the box". There is no need to worry about server, database, software installing, updates and backup. You may also eliminate all non core business from your company to establish simple and effective workforce management without any IT expert. All you need to have is a click on Internet access. Ideal solution for business on several locations that are not connected in a single VPN network, BoneID W3 on Cloud makes them connected when it comes to Access Control and Time & Attendance. Different level of instance sharing in computation power makes it suitable for any size of enterprise with unlimited user and devices. Department tree hierarchy of workers in almost every interface for easy management Employees List will show all active employees for selected department or all active employees if departments control is not present. Date selector is simplified control for selecting desired period we want to process.
Add to Compare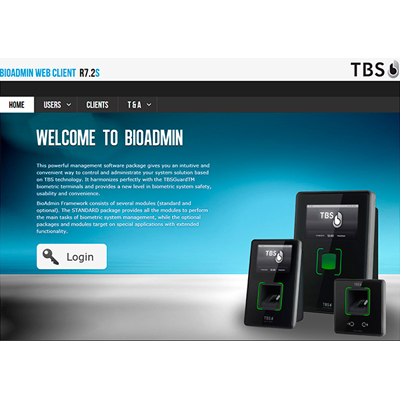
TBS BioManager is a web-based management software, installed either on a local or on a cloud server. It features user and device management, rights management, alarm management and much more. Adminstration of all users in the biometric installation, with options to edit, filter and sort. Moreover allows to enrol user biometrically directly in web browser.
Add to Compare
BioConnect has taken a platform approach to biometrics -- Its core identity platform enables organisations to easily consume current and future biometric technologies as an authentication strategy, delivering greater security, assurance and convenience along the way. With multiple software and hardware-level integrations, BioConnect has developed a standard way of integrating and deploying biometric solutions within an existing infrastructure. From a software perspective, its advanced plugin architecture results in seamless synchronization of all data. This means that with each new install, site expansion, or upgrade enterprises and system integrators alike can feel more confident in the installation pre- and post- install. The result is a more effective way to scale biometric systems and maintain visibility across an enterprise, globally.
Add to Compare
When scores of visitors pass through the entrances of large facilities, ineffective visitor management can compromise the security afforded by significant investments in perimeter security and access control.Honeywell's award winning Electronic Visitor Management System LobbyWorks™ can contribute substantially to the safety and protection of both personnel and property. The ability to automatically screen and track visitors is an essential part of a complete security plan.The LobbyWorks™ Suite offers a simple and cost effective way to:Determine who is in your facility at all times Identify unwanted visitors Eliminate abuse of visitor badges Protect the confidentiality of visitors Facilitate communication between hosts, visitors, and security personnel Improve lobby and security desk productivity
Add to Compare
CNReader SDK is software development kit worked with CN3XX and CN6XX product series for second development. It includes API, Host Demo,user manual,USB driver and programme example. It's developed by C++builder developing tool on Windows Operating system and GCC developing tool on Linux OS, compatible to VC, VB/VB.NET, C++, C#.NET, DELPHI etc. It also offers special Host Demo and API for MIFARE Plus® and MIFARE® DESFire® EV1, NFC and SAM. Hightlights: SDK is available with some special benefits for customer’s development Stronger and powerful informative API to save your time and cost for development Examples for good reference and understanding, using developing tools like Delphi, C++ Builder, C#, .NET, VC, VB/VB.NET etc. APDU channel packaged into API to operate all commands of smart card Comprehensive platform to provide flexibility by customer side: Operating System: Android,Linux and Windows. Support Win 98,Win ME, Win 2000, Win 2003, Win 2003 x64, Win XP, WinXP x64, Win Vista, Win Vista x64, Win2008, Win2008 x64, Win2008 R2 x64, Win7, Win7 x64, Win8 Host Demo, a software testing tool to ease and simply development
Add to Compare
TBS Cloud Services takes care of: Setup and upkeep of the server Installation of the server software including updates and upgrades Data storage, data security, and data protection Guaranteed availability E-mail and telephone support for all questions about the server software Advantages: Outsourced solution for good value – with stable costs you can plan for Server and software are always up-to-date The highest level of security and availability Remote access via any browser-enabled end device
Add to Compare
WinDSX was designed and engineered for the central monitoring of multiple Locations using dial-up modems, direct serial port connections, and/or TCP/IP communications. WinDSX is commonly used for applications as varied as 1 PC and 1 reader to multiple PCs and hundreds or thousands of readers. WinDSX can be used on a single PC with a single Location connected but exhibits its true power when used on a LAN controlling multiple sites, both local and remote, from a central station environment.
Add to Compare
A Mobile access is changing the way we interact with buildings and how we manage their security. The smartphone becomes a mobile key just as easily as it transforms into a payment card or a map. With this convenient device, users unlock buildings or rooms, across one or multiple sites, securely and at a lower cost to a business than alternative credentials. Mobile access via Aperio battery powered locks is built on Seos, a next-generation platform with class-leading cryptography and authentication, plus unrivalled privacy protection. Security managers can amend mobile credentials over the air, without any need for dedicated readers or asking a user to check-in their credential. Nobody is left waiting around for their access permissions to update. Compatibility and security are at the heart of Aperio mobile access. Aperio locks already accept all major RFID credentials as well as the NFC mobile wireless protocol. The E100 Electronic Escutcheon works with Bluetooth Low Energy (BLE) too. More Aperio devices will offer BLE compatibility in a near future. User experience at the door is always identical. Users simply present their Android or Apple phone at the reader, just as they would a smart-card. They don’t even need to open an app. No training is needed, because unlocking an Aperio device is easy and intuitive. Aperio locks can operate with all credential technologies simultaneously: Building users need not unanimously adopt one format. Security managers do not have to implement a mass transfer to a single technology. Businesses can run RFID and mobile in parallel. They can upgrade from low- to high-security credentials when they choose. Every technology is always included in the package: There is no decision to make at the moment of purchase. Aperio locks already reduce the cost of extending access control within a building, wire-free. They are quick to install, cost-efficient to run and integrate seamlessly with security systems from over 100 different manufacturers.
Add to Compare
Building Automation - The WinDSX Software is capable of controlling a number of Building functions. Equipped with time, date, day of week, user, and event driven relay outputs the system can virtually control anything that is electrical in nature or can be controlled with a switch or timer. Most buildings have a vast electrical system that supports lights, signs, fountains, HVAC, elevators and more.
Add to Compare
DSX Database Management API can be used to develop an interface to add/edit/delete data in a WinDSX or WinDSX SQL system. It can be used to place the initial data into the system and it can be used as a real time interface for ongoing data manipulation. It is a document that outlines the use of the DSX Markup Language which allows for the Card Holders to be added, deleted and maintained from another system without compromising the integrity of the database.
Add to Compare
Deny particular groups of carriers access to certain zones in special situations, for example during crises or when dealing with various threat levels. System administrators can (de)activate Verification, APB and Counting for each of these special carrier groups. The number of security levels that can be set with this licence is unlimited.
Add to Compare
SMARTair™ from TESA makes affordable access control more flexible and more mobile than ever with the Wireless Online management system. With just a couple of clicks using the Web Manager, facilities managers can configure their access control system, remotely unlock doors, view what is happening in the facility and much more, wherever they are in the world. All you need is a web connection to manage access control with the new Web Manager. With a standard browser such as Chrome, Internet Explorer, or Firefox, and without any additional software installation, you can remotely and securely open your organisation’s wireless devices from anywhere. The SMARTair™ Wireless Online system management from TESA does more than just remote unlocking. The simple interface also allows security managers to receive system status updates, set automatic email alerts, change a user’s access rights, or examine an audit trail, from anywhere in the world. Server communication security is ensured thanks to the HTTP Secure (HTTPS) protocol, which uses the latest encryption methods (SSL/TLS). Facilities managers can also enjoy the same functionality and simple interface by installing the SMARTair™ app. The app is compatible with iOS, Android, Windows and BlackBerry devices, and can manage multiple sites from the same simple interface.
Add to Compare
Airlock is not an Access Point itself but synchronizes multiple Access Points in such a way that only one can provide access at a time. Furthermore, it is capable of controlling the occupation of the lock. When connected to Airlock an Access Point will always ask the Airlock for exclusive rights to provide access. Since Airlock will only grant the exclusive rights to one Access Point at a time and the Access Point will release the exclusive rights after closing the door, only one door can be open at a time. This synchronization function applies to Badge handling, Manual unlock input, Provide access (server). The synchronization function does NOT apply to Emergency unlock input, Automatic unlock schedule, Access control de-activated and unlocked (server).
Add to Compare
Standalone/Network or server management Solution for unlimited number of users Support various types of access levels to enhance security 4 Customisable job code for In/Out manage Each event record stores actual user picture to prevent misuse of card Flexible data transmission via TCP/IP port, or Wi-Fi, GPRS for wireless communication Customisable Skin and LOGO and easy setting for all parameters by one touch Multi-language software supports most common world languages and is simply to translate into any language
Add to Compare
The Global Client Programme also ensures your access control is cyber secure, future-proof and secure by design, so it’s easy to adapt your system to future trends and risks. And it keeps your budgets in check while giving you a physical access control system that’s: Unified internationally Locally compliant Always up-to-date The key benefits of using the programme rather than handling a global security rollout internally are the ease of achieving both international standardisation, flexibility, scalability, cost efficiencies and faster implementation.
Add to Compare
The Identity & Authorisation Application means lower costs and higher security. Because it has an attractive, intuitively usable interface, there is virtually no need for training. The ability to multitask leads to higher productivity and improved customer service. Thanks to widgets, every functionality can be accessed quickly and efficiently. And if a task needs high attention, all other functions are moved to the background.
Add to Compare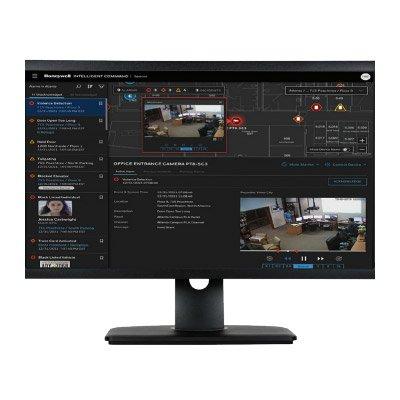
1 server license, 32 reader licenses, 1 concurrent User license, 1 concurrent advanced badging license Web Based Client for Badging, Reporting, Alarm and Event Monitoring Mobile Client for Badging, Badging Verification, and Door Control Server support including Windows® Server 2022/2019, Windows 11 (64-bit), SQL Server 2016 SP1, 2017 and 2019 Single user interface for multiple security and business functions Pro-Watch via Honeywell Software Development Kit (HSDK) can be integrated with other building systems such as secondary fire, lighting and heating, ventilation, and air conditioning Web Services API enables Integration to third-party systems and Active Directory Certification Management Event/action associations including sending emails, running a stored procedure, or triggering a panel I/O point Pro-Watch-level triggered events for panel-to-panel and panel-to-software actions or within a panel for local actions Advanced Reports Support for Microsoft Azure Virtualisation support for VMWare and Microsoft® Hyper-V Compliance Reports that offer data and statistical reporting; auto generated reports upon schedules Easy system setup and maintenance with user definable hardware templates Database partitioning and definable operator permissions
Add to Compare
Reliance High-Tech - an Elite member of the Honeywell Systems Integrator Programme - has selected Honeywell's WIN-PAK™ PRO Central Station software to power its new managed access control solution. The service, which will be hosted by the dedicated Reliance Monitoring Centre in West Yorkshire, will potentially generate significant additional monthly recurring revenues for Reliance through the provision of ongoing remote managed access control services to its customers. Remote managed access control presents the ideal security solution for both Small to Medium Enterprises wishing to install access control for the first time, as well as existing access control customers who want to switch from a locally based system to a more cost effective and flexible remote managed solution. The WIN-PAK™ PRO Central Station remote managed access control software from Honeywell will reduce installation and service costs for both Reliance High-Tech and its customers in a number of ways including removing the need for dedicated on-site PCs at customer premises, reducing end-user training requirements and facilitating remote servicing. The scalability offered by remotely managed access control will also allow Reliance High-Tech to quickly and easily adapt security solutions, depending on its customers' needs. As part of the service, Reliance High-Tech monitoring specialists will be able to remotely open and close doors on request, create customised security reports for customers and respond to on-site alarms, alerting emergency services where necessary. Customers can also access the system remotely at any time through a secure web portal if they need to add/delete badges or view the latest reports in real time. Initially set up to provide CCTV and access control support for its customers, the BS5979 Cat II Reliance Monitoring Centre quickly diversified its services to include command and control, lone worker protection and asset tracking. The centre works in accordance with ISO270000 for data protection, and has a separate mirrored centre 60 miles away for contingency purposes. This latest move to extend the offering to include remote managed access control came in response to a growing customer demand for the innovative service. Reliance High Tech's long standing relationship with Honeywell made the task of choosing a technology partner for the service a simple one. "Reliance High Tech has been installing Honeywell WIN-PAK™ technology for many years and our teams are extremely familiar with the strong technical capabilities, user friendly interface and database management functionality of the range," said Dan Thomas, sales and marketing director, Reliance High-Tech. "The addition of WIN-PAK™ PRO Central Station to our access control portfolio helps our customers to save money by reducing manpower and using technology more intelligently to enhance security.""In today's security environment, many organisations seek the protection provided by a comprehensive access control solution but do not want the financial burden of hosting the system locally," said Daniel Wan, UK marketing leader, Honeywell Systems Group. "Outsourcing security functions to experts such as Reliance High-Tech offers an excellent solution and allows organisations to take advantage of the very latest security technology from trusted brands like Honeywell, while simultaneously reducing overhead costs incurred."
Add to Compare
1 server license, licenses for 96 readers, 1 concurrent User license, 1 concurrent classic/advanced badging license Web Based Client for Badging, Reporting, Alarm and Event Monitoring Mobile Client for Badging, Badging Verification, and Door Control Server support including Windows® Server 2022/2019, Windows 11 (64-bit), SQL Server 2016 SP1, 2017 and 2019 Single user interface for multiple security and business functions Pro-Watch via Honeywell Software Development Kit (HSDK) can be integrated with other building systems such as secondary fire, lighting and heating, ventilation, and air conditioning Web Services API enables Integration to third-party systems and Active Directory Certification Management Event/action associations including sending emails, running a stored procedure, or triggering a panel I/O point Pro-Watch-level triggered events for panel-to-panel and panel-to-software actions or within a panel for local actions Advanced Reports Support for Microsoft Azure Virtualisation support for VMWare and Microsoft® Hyper-V Compliance Reports that offer data and statistical reporting; auto generated reports upon schedules Easy system setup and maintenance with user definable hardware templates Database partitioning and definable operator permissions
Add to Compare




