Access Control Softwares (653)

Premier Elite V2.02 firmware is contained within the latest version of Premier Elite Flasher Interface software. The Premier Elite Flasher Interface can be used to update the Premier Elite Control Panels firmware, allowing additional features and functions to be added to existing systems.
Add to Compare
There are four main report templates: activity, cardholder, evacuation and exception, these can be scheduled and automatically generated. When the optional notifications feature is deployed, these reports can be automatically emailed to the relevant people. Other reports which can be generated from operator workstations are: Access and access groupsContact ID assignment Electric fence voltage Site configuration Time and attendance Wiring Options to include brand elements and customise report layout as well as flexible output options ensure your reports are tailored to your requirements.
Add to Compare
SALTO HAMS Department Operator is a hotel access management software for control of hotel access and guest management. It can manage unlimited on line doors and up to 40,00,000 users. It also features department operator management. Both guest rooms and back of house doors are managed in one system and it can control both off line and on line units centrally. The software is network ready.
Add to Compare
Scalable access control and security management solution for large organisations Unlimited client workstations, card readers, and card holders Support for 64 bit operating systems only Employs the very latest in user interface design Fully network compatible using minimal bandwidth Cluster aware version available and virtualisation support Video Badging and Visitor Management software as standard Card numbers are optional, allowing Cardholder records to be created without a credential Database partitioning for multiple company or departmental systems Comprehensive alarm handling features Fully integrated Symmetry Video Management Open architecture with numerous integration options Uses Microsoft SQL Server Database
Add to Compare
Photo ID and Encoding is an optional licensed feature available in Gallagher Command Centre, providing the ability to design and produce encoded and/or photo identification cards. The information retrieved from the Gallagher cardholder database would typically include the cardholder’s photograph and access credentials. However, there is an extensive range of options available with this Gallagher optional feature for formatting card layouts, including: Creating backgrounds Importing logos and imagesAdding and formatting textIncorporating barcodes Personalised cardholder data
Add to Compare
Bosch Security Systems further enhances its widely-used access control solution for small and medium-sized companies with the Access Professional Edition (APE) 2.1 which will be released soon. Thanks to new interfaces, an even larger number of devices and operating systems are now compatible.Since its initial launch, the easy-to-use, scalable access control software APE meets an extensive range of security requirements and assures an easy integration of access control with a variety of security functions, such as CCTV, intrusion detection or elevator management. In its updated version, APE features an optimised support of the most common operating systems, such as Windows 7, Windows Server 2008 and Windows XP. Furthermore it enables a seamless interconnectivity with Bosch HD cameras and the midrange recorders Divar 400 and Divar 600.With APE, Bosch offers a multifunctional, extremely reliable yet flexible solution for a variety of small to midsized establishments such as office buildings, laboratories, schools or the likes. The system is capable of handling up to 10.000 cardholders. In total 128 readers and 128 cameras can be managed. The access modes ‘card', ‘pin' or ‘card and pin' provide individual levels of security."APE is very popular with our clients, as it caters to all common security requirements and offers a number of additional, handy features", says Patrick Looijmans at Bosch Security Systems. By displaying the database photo and a live image recorded at the door, as well as basic cardholder data with the time stamp of access request for example, the software helps the operator to instantly verify that card and cardholder are matching. Also a fast tracking of persons in the building is possible, which is particularly helpful in case of an emergency. Using the integrated card configuration function furthermore increases the security as badges can be designed according to corporate guidelines and persons can be identified throughout the entire premises. "All in all APE is a modern, straightforward all-round solution, which just got even better in its latest version 2.1", says Patrick Looijmans.
Add to Compare
Anviz CrossChex is a personnel identity verification, access control and time attendance management system. The system facilitates management of personnel information by biometric technology and helps meet customer's time attendance and access control requirements. CrossChex Cloud is a cloud-based time attendance software and can be used to access data anywhere, anytime, from any browser. You can schedule attendance requirements for a specific employee and create shifts for their work period within one click. During this global pandemic, CrossChex Cloud can work with Anviz biometric time clocks to enable users to check whether their employees are wearing a mask or not, and get timely reports on - employee attendance record, entrance record, and temperature record.
Add to Compare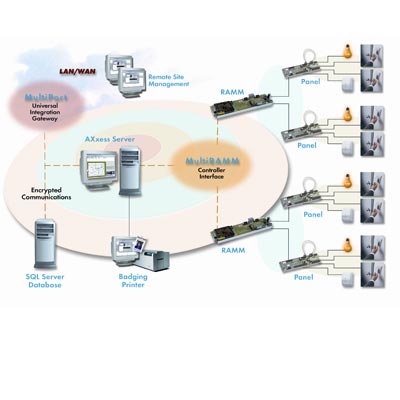
Encrypted network security management software package. Features encrypted network communication to door controllers and PC workstations; unlimited number of doors; unlimited system access levels, operators, time tasks & time zones; multi-language support; integrated CCTV control and video badging. Supports multiple workstations and simultaneous use of multiple site codes and Wiegand formats. With global anti-passback and elevator floor control.
Add to Compare
User/Cardholder ManagementThe incredibly flexible user permissions provide an easy-to-use, building block method of assigning access and security rights to cardholders. Cardholder profiles are easily created by assigning multiple permissions with simple “Allow” and “Deny” functions. ReportingSingle-click reporting to review the areas cardholders have accessed, what areas cardholders have access to, search event and alarm history, programming history and much more. Easily export reports in a variety of common file formats. Schematic MapsRich graphics with interactive floor plans and maps. Effortlessly create maps using the built-in library of animated icons. Security and Alarm ManagementComplete alarm management with powerful automated actions. Operator PermissionsManage the operators that use Integriti software. Easily customise and define their access permissions levels with fine control. Audit TrialThe amazingly powerful forensic audit trail records every programming change made by all operators and provides the ability to “roll-back” to any change in the past. Data ImportationImport cardholder data in a variety of file formats from third party systems. System Health MonitoringMonitor the health of both the Integriti hardware and software. Proactive notifications can alert security operators and security contractors if maintenance is required. SkyTunnel ConnectivitySkyTunnel is an industry-first cloud based service that provides hassle free connectivity of Integriti hardware, software and mobile apps. Intuitive DesignThe Integriti System Management Suite is a true cutting-edge solution. Integriti boats a contemporary and intuitive design that is simple to use and easy to learn. System Designer and GateKeeper ApplicationsSystem Designer is used for all aspects of system programming and configuration. GateKeeper is a dedicated application to simplify day to day monitoring and control of the Integriti system. Modern Client/Server ArchitectureIntegriti employs a client/server architecture and is fully compatible with the latest computing platforms and Microsoft SQL databases.
Add to Compare
Personalized actions are individually programmed responses that are configured for individual cardholders or an access group – such as switching on lighting or air-conditioning in a specified zone. These responses are initiated on a cardholder’s ‘access granted’ or ‘access granted and taken’ event, with up to 250 individual cardholders or access groups able to be defined for each access zone. All authentication methods to identify the cardholder are supported, including, for example, PIN only access events and those from third-party systems integrated via the Controller application programming interface.
Add to Compare
Secu365 is built specifically for small and medium business owners, simplifying security interactions for property managers, tenants, employees and visitors. Regardless of what type of service you provide, if you have a brick-and-mortar business, a well-rounded and easy-to-use security system is not just important—it's essential. Just take a look at a few of the benefits that you might be concerned about and get from the business security system Monitor customers and employees with video surveillance in case of any accidents that happen Help prevent theft, vandalism, and other crimes With a mobile device, remotely control your business from anywhere Furthermore, as businesses continue to maintain a mostly remote workforce, the drive towards adopting cloud-based and hybrid solutions has grown as well. Thus, with 24/7 video monitoring, indoor and outdoor cameras, integrated with biometric or mobile access—Secu365 system is the perfect way to protect your small business. It enables visual multi-validation of alarm events and real-time remote control.
Add to Compare
SALTO Pro Access Department Operator access control software can manage unlimited on line doors and up to 40,00,000 users. It also features department operator management. It allows to program access time zones for each user, take into account different company calendars, obtain audit-trails from the door to see who has passed through it, and it includes special functions like automatic changes of the door status, anti pass back and relay management (i.e. elevators control). It can manage large numbers of door installations, and as most access related information is written on the credential, the management of the doors becomes, in cases, a management of the credential. By simply updating the badge, most access related authorisations of the users can be changed, including adding/deleting doors, time zones, calendars etc.
Add to Compare
Specialist Access Control provider TDSi is bringing together the benefits of its entry control products with other perimeter security and building services controls, by offering full interactive systems integration. Earlier in the year TDSi launched a module for true TCP/IP integration from its EXgarde PRO software suite to alarm specialist Texecom’s Premier range of Intruder Alarm panels. The solution allows full integration to other serial based devices such as IP CCTV, TDSi’s VUgarde NVR providing visual verification of Intruder Alarms through TDSi’s EXgarde PRO. John Davies, Managing Director of TDSi, comments “Integration with Texecom has enabled TDSi to augment EXgarde PRO into a more complete and truly integrated surveillance and security system at the TCP/IP level. The user has full control, being able to arm and disarm zones to suit the use of the building, reducing the number of false alarms triggered, and providing visual verification of alarms.” Integration provides enhanced control and offers numerous benefits, such as the ability to activate and deactivate specific panels across multiple sites, as well as individual zones of a building and the ability to monitor all Intruder Alarm events which appear in the EXgarde Pro Alarm Manager Events panel. If an alarm is activated, CCTV can be triggered to deliver both a real time image and a 15 second pre alarm condition recording to the control room. The integration also means users benefit from a single point of administration with the ability to monitor a log of the intruder alarm system and also reduce the numbers of false alarm and the problems associated with this. This add-on to EXgarde continues TDSi’s overall commitment to making systems integration easier. The other key features of the system include the ability to log events in EXgarde, view the alarm zones’ status “armed”/”part-armed”/”disarmed” in EXgarde, remote arm/disarm from access events and part-arm zones from access events. These flexible features allow users to avoid costly false alarms through arming only required zones of a building, also preventing unauthorised people from accessing certain zones. TDSi also recently announced the launch of the new Harmony Security Alliance, with even broader aims to ‘Collaborate, Innovate and Protect’ across the security product offering spectrum. TDSi is partnering with exterior detection equipment specialist GJD Manufacturing and specialist in highly efficient power supplies Elmdene International Ltd - along with Texecom, to offer installers and end users an unrivalled integrated service for all security and access control needs. The Harmony Alliance also means that the partner members will co-operate and develop on-going solutions that are designed to complement each other and work together effectively, whatever the specification of the overall system that is installed. For further details on TDSi and its range of access control solutions, please visit www.tdsi.co.uk or telephone +44 (0)1202 724 999. Installers and end users who would like more information on the Harmony Alliance, and have specific project requirements, can find further details on the new dedicated website: www.harmony-alliance.com.
Add to Compare
SALTO Access Connected access control software can manage unlimited on line doors and 40,00,000 users. The features allow to program access time zones for each user, take into account different company calendars, obtain audit-trails from the door to see who has passed through it, and it includes special functions like automatic changes of the door status, anti pass back and relay management (i.e. elevators control). It can manage large numbers of door installations, and as most access related information is written on the credential, the management of the doors becomes, in cases, a management of the credential. By simply updating the badge, most access related authorisations of the users can be changed, including adding/deleting doors, time zones, calendars etc.
Add to Compare
OnGuard GO! supports up to 32 devices (64 readers), 5000 cardholders, 32,000 access levels, 8 card formats, 512 inputs, 512 outputs, up to 30 transactions per minute and a USB capture device. The system also supports peripheral devices with industry standard communication drivers, including credential printers (Nisca, Eltron, Magicard), network connectivity devices (Lantronix) and readers (magnetic stripe, Wiegand, proximity, bar code, smart card and biometric).
Add to Compare
Access PE provides self contained access control for small and medium-sized companies. Its installation is extremely simple and fast. There is no need to install and administer a database system. The system is easy to use and enables a person with minimal training to create badges and administer access rights in a very short time. Specific event logging and reporting allows you to trace who was when and where on your company’s grounds.
Add to Compare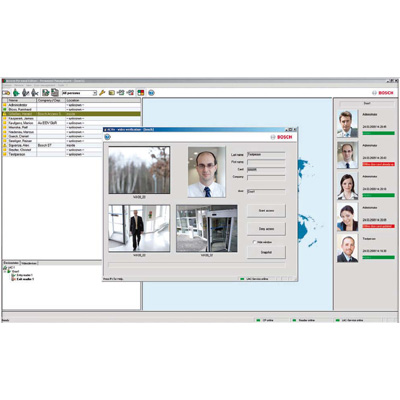
Following the Security 2010 exhibition in Essen, Germany, it is evident that Bosch is receiving increased awareness for its investment in the access control and integrated systems markets. While the Bosch booth has traditionally been popular for its video, communications, intrusion detection, and fire prevention solutions, this year Bosch saw an exponential increase of interest in the access control and integrated systems offerings, making it yet one of the areas of highest growth potential.In Essen, Bosch showcased its complete portfolio of access control and integrated systems solutions. Customers were able to see and experience solutions for small, mid-sized and large environments: the Access Easy Control System supporting up to 32 readers, the reliable 128-reader Access Professional Edition system, and the Building Integration System (BIS) software. The BIS software system is used to connect all security, safety, and building automation components and to integrate them into one central and comprehensive management system.Further to the enhancement of the portfolio itself, Bosch is increasing its market presence with additional service offerings and more trained marketing and salespeople to answer the growing demand. According to Alex Squarize, Bosch Security Systems, "Bosch is absolutely in a good position for future growth. The investment in research and development over the past years has already started to pay off. We are adding to our portfolio day after day, while we continue to invest into training and development of our employees. No other company in the market is currently investing as much into access control and integrated systems solutions.""The future outlook remains positive", Squarize continues. "We are currently seeing more and more implementations of these Bosch solutions, and we are experiencing substantial growth in both geographical reach and quantity. We look forward to 2011 with optimism!"Download PDF of Bosch Access Easy Control system
Add to Compare
CrossChex Mobile is the mobile version of CrossChex Software, which lets you add and manage everyone and grant access rights to them on a smartphone. Your staff can easily clock in and access to any places with just one click on the phone. Any of Anviz access control devices with Bluetooth function can be added to CrossChex Mobile, and the time attendance device with Bluetooth function can be also added to CrossChex mobile to have a clock in function and realize the access control function with linked to a Bluetooth micro access controller. CrossChex Mobile is suitable for the application in small offices, retail stores, gyms, clinics, etc.
Add to Compare
Notifications is an optional licensed feature for Gallagher Command Centre that enables email or text messages to be sent to cardholders about events and alarms, as well as the imminent expiry of their cards or competencies. Notifications from Gallagher Command Centre are sent as email via a site’s mail server. To support notifications via SMS the site must subscribe to a ‘Bulk SMS Service Provider’. The Gallagher security system communicates with this provider via email specially formatted for final delivery via SMS. The provider then converts the email received from the Gallagher system to an SMS message and forwards it to the appropriate mobile network provider.
Add to Compare
Web-base software Supports multi-languages Supports LILIN access controllers Supports LILIN IPCAMs and NAV Time sets: 255, time zones: 33, holidays: 100 can be set Supports cardholders up to 20,000 and dept. up to 100 One door can set up to 3 IP cameras E-map: Support camera live viewer and real time event log Open and close doors via network Sends E-mail notification when the alarm event occurred
Add to Compare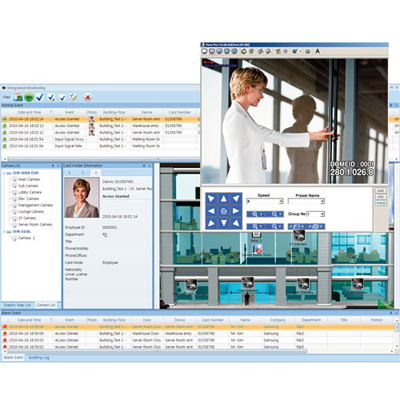
IDTECK, Inc. has released iDWATCH integrated management software, which provides high level of security by integrating video surveillance with access control system.iDWATCH IAD PRO I/II are advanced integrated security software, which allow integrated monitoring of video surveillance and access control. Multiple numbers of DVRs can be networked together (Distributed installation of DVR and management software) with the access controller for management of large business management and allows multi-site management and monitoring using the server/client support.iDWATCH IAD BASIC I/II are advanced integrated security management software, which is designed to centrally monitor video surveillance and access control. These softwares are suitable for small size business such as convenient stores, offices, storage areas and etc. This system is offered in standalone system (DVR with embedded management software) and when installing several DVRs, it allows integrated video monitoring using the iDWATCH CMS.Enhances the security level as the video surveillance visual data is added onto the access control data in textHelps the administrator in take measures for the event as the user's image is captured along with the alarm eventPrevents proxy attendance or buddy punching as user ID and video image are comparedOffers high efficiency in management as access control and video surveillance are integrated in a single softwareHigh security guaranteed at affordable installation costReal-time monitoring and management via remote control
Add to Compare
In the past the Access Control industry was a relatively straightforward one. Vendors supplied access control systems to installers who in turn organised and fitted solutions which were primarily concerned with securing doorways and controlling the flow of people traffic to restricted parts of the premises. But like most parts of the security industry, the Access Control sector has evolved and the industry is looking to expand their offering to add more value for money than ever before. For some this would have been unthinkable even a few years ago, but now successful companies have to think outside the traditional boundaries to meet the constantly evolving expectations of the market. Integration is a word that is mentioned time and time again in relation to Access Control – and with good reason! The IP revolution has become just as central to this sector as the rest of the security and wider technology world and has shaped the expectations of customers. Far from being a novelty, any system that doesn’t integrate with other IP systems at some level is now considered unusual. The move towards integration means that mutually communicative systems are essential, with the likes of Microsoft Active Directory becoming a central hub to all kinds of company systems from security to Human Resources and Facilities Management systems. As an extension to this, there are also demands for solutions that can still incorporate older legacy systems, which in all likelihood would never have been designed with this kind of integration in mind. For example, a company that has a large installation of analogue CCTV cameras (which may well still have a high degree of their effective lifecycle remaining) is unlikely to want to tear them all out in favour of more modern IP megapixel cameras, just for the sake of having new ones. Modern integrated systems can deal with these integration issues, but it is something that installers need to be sympathetic to, offering solutions that will save their customers wasting budget and will offer tailor-made, highly relevant solutions. The modern business world is largely responsible for driving the need for integration. Security and the ability to monitor and prove it are high priorities, but so is doing it effectively on tighter budgets. Rather than seeing it as a potential stumbling block, the Access Control industry needs to see the opportunities to offer customers a sizable and crucial part of the wider security offering. Schools are a good example of the need to integrate all the security systems to protect potentially vulnerable users. Modern educational establishments usually use a dedicated Schools Information Management Systems (SIMS) which gives a single point of administration and reference. With this at the heart of the establishment, the opportunities and benefits from creating a two way communication between the SIMS and the access control systems is obvious. For an installer there may be a temptation to sell the school a simple, standalone access system (particularly when budgets are under such close scrutiny), that offers lower upfront costs with a simpler installation process - yet there is a superb opportunity to offer a hard working solution that may cost more up front, but will really make good use of existing systems, offering far bigger rewards and helping to future-proof itself for considerably longer. The concept of thinking outside the box can apply on many levels. Access Control is closely linked to security and yet an integrated system can be as much a part of the management of the wider buildings’ control systems. If a people counter system can be used to ensure perimeter security access isn’t breached, then why not use it to control heating and ventilation? Closely controlling these systems minimises the waste of resources whilst ensuring users still get the services they need. Another area that is ripe for the help of Access Control as a value-add is Health and Safety. Being able to monitor the number of people who enter a controlled area also means a close eye can be kept on occupancy. Not only can this control the access of unauthorised people, it also monitors if a lone worker is present in a potentially hazardous area for example, alerting other members of the team that there may be a risk to their safety. Linked to this, it can also be an integral part of compliance, logging when staff are present in a hospital or a prison for example, integrating directly with the employment management system to provide highly accurate and secure information. The humble MIFARE card is another industry standard that can actually offer users a great degree of flexibility and empowerment beyond its Access Control role. The secure identity information held on the card can easily be accompanied by additional authentication details which are just as safe. Businesses or organisations that require a number of different secure functions (such as a university campus for example – which may offer library, gym membership and EPOS systems for retail) can use a MIFARE card as a single confirmation token. The appeal for our customers is that it reduces cost by utilising existing system investments to provide new services, whilst being relatively simple to implement. These examples of ‘Thinking outside the box’ could just be the tip of the iceberg as new technologies are waiting to grab the market. Near Field Communications are rapidly coming into focus as a security tool, building upon the popularity of smartphones and mobile devices on which they are deployed. This is an exciting technology as it utilises a ubiquitous everyday device to offer secure and convenient authentication which as mentioned above, can have a myriad of different uses well beyond the traditional access control arena. Biometric authentication is another area that is coming on in leaps and bounds. Being able to use a fingerprint, retina scan, facial recognition, sub dermal scan or even the analysis of the circulatory system, frees users from having to carry a token and yet offers even tighter levels of security. These levels of security will make it even easier to integrate different systems and the idea of limiting the potential of access control will seem like an anarchistic relic of a bygone age.
Add to Compare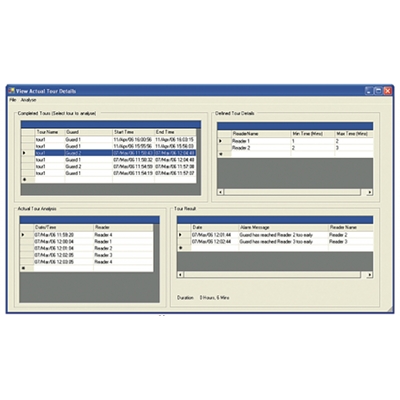
Additional features gives eXguard PRO the ability to integrate with equipment from the leading CCTV or biometric reader manufacturers. Maximum flexibility and ability for software to be tailored to exact specifications.
Add to Compare
Upgrades Velocity Single User, Server and Client application software from previous version to the latest version. Includes support for new installations for backup and ongoing expansion. Includes latest downloadable firmward for CCM-F to upgrade DIGI*TRAC controllers (CCM-F not included). Includes CD-ROM, Install Guide. NET*Adapt is not included. Specify version for updating to by replacing the XX with the version (e.g. VEL-UPD3.0 for upgrading to Velocity Version 3.0).
Add to Compare
Access control has become a vital component of any security concept worldwide. The protection of intellectual property rights, prevention of theft and sabotage or simply compliance requirements - there are a multitude of reasons why companies of all kinds need to use a comprehensive access control system to restrict, manage and control access to their facilities. However, operated in isolation from other safety and security systems, even the most sophisticated access control system cannot really live up to its promises. In such an environment, operation and monitoring can quickly turn into a nightmare, as each system has its own architecture, its own user interface and its own management tool. This is why more and more organizations are looking out for an access control solution that easily integrates with video monitoring, intrusion detection and sometimes even visitor management to form a homogeneous security system with a consistent user interface and central management and operations.Moreover, suppliers are more and more often faced with requirements of their customers to supply a documentation of all access attempts, whether successful or not, to protect against industrial espionage. To fulfill this requirement, not only employee access must be captured and recorded, but also the entire visitor traffic. Video integration for more safetyWhile modern access control systems allow an efficient management of access rights, they are rather powerless against abuse if operated on their own. In critical environments it is mandatory to add a second layer of security by integrating access control with some kind of video surveillance. To prevent abuse, all access requests can then trigger one or more video cameras. Integrated systems can provide alarm verification, instantly displaying live video images from nearby cameras when there is an alarm event at a door - such as when a person presents an unauthorised credential or when a door is forced open. Forensics can also benefit from such integration if the video recordings are referenced in the access control system's event log. Such a feature greatly facilitates identification, retrieval and playback of past events and alarms if necessary.Open standards ease integrationIntegrating access control, video monitoring, and intrusion detection can be rather easy when all components come from the same vendor and if this vendor also offers a management platform like the Building Integration System from Bosch for all of them. Integrated systems "off the shelf" can greatly ease installation and configuration of the security solution. Logical integration eliminates the need for multiple software platform and interfaces -- resulting in fewer complications and greater event-driven functionality as well as reduced installation time and costs. What's more, this kind of integration also promises more efficient operation and a clearly reduced need for training, but above all also a higher security level. An open standards-based management system even makes sense in those cases where one vendor supplies everything, as it opens up the entire installation for future expansion.User interface is keyAn integrated security system is a very complex apparatus, and if this complexity is not hidden from the user, the system will be highly prone to human error and maloperation. Such systems do need very clear and intuitive user interfaces, avoiding information overload while offering all the information that is currently needed. This is even more important when several components or dialogs are open, which will often be the case if you deal with access control, video surveillance and maybe intrusion detection from the same console.
Add to Compare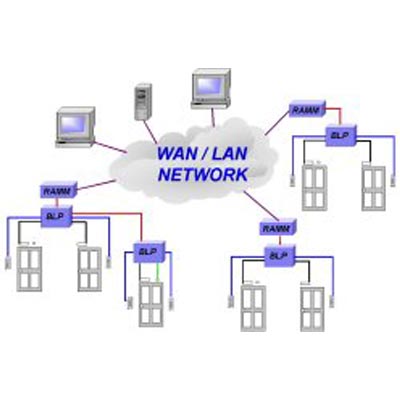
Encrypted network security management software package. Features encrypted network communication to door controllers and PC workstations; unlimited number of doors; unlimited system access levels, operators, time tasks & time zones; multi-language support; integrated CCTV control and video badging. Supports multiple workstations and simultaneous use of multiple site codes and Wiegand formats. With global anti-passback and elevator floor control.
Add to Compare
ISONAS has taken its Software Development Kit to the next level and now offers a simple integration with the ISONAS Pure IP™ hardware solutions, giving customers real choice in their access control hardware. Access control evolution Partners can now create a powerful solution and add the next evolution in access control hardware to their product selection; while benefiting from future proofing their selections, reducing costs and giving them choice in their access control hardware. This comprehensive software development kit from ISONAS, makes it easy to integrate 3rd party access control software with the ISONAS Pure IP hardware families. ISONAS SDK platform While other SDK’s use low-level, error-prone TCP/IP communication to integrate, the ISONAS SDK platform supports high-level management mechanisms for event management, local discovery, communication and configuration. Using the .NET framework, the ISONAS SDK allows users to customise which features and functions of the ISONAS hardware to implement. With the ISONAS SDK, partners can add choice to their access control hardware solutions and go to market in no time. An open platform philosophy is nothing new to ISONAS. The company has a long history of integrations and with this significant investment into a modern SDK, ISONAS is furthering its mission to become a global player in open architecture hardware and software.
Add to Compare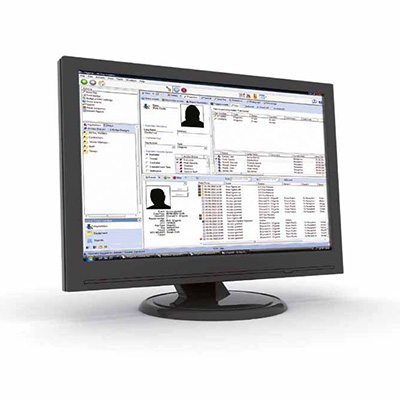
EXgarde is a fully featured Access Management PC software application that combines an extremely intuitive graphical user interface and powerful integration capabilities in a single package. Supporting multiple doors as standard with the option to extend this with an unlimited door licence, EXgarde meets the needs of even the largest of access control networks. With EXgarde PRO integration and expansion are key features and there are numerous possibilities to integrate with the latest CCTV and biometric technologies.
Add to Compare
Upgrades Velocity single user, server and client application software from Verson 2.0 or later to the latest version. All intermediate Version Updates. Includes support for new installations for backup and ongoing expansion. Includes latest downloadable firmward for CCM-F to upgrade DIGI*TRAC controllers (CCM-F not included). Includes CD-ROMs, and Install Guides. NET*Adapt is not included.
Add to Compare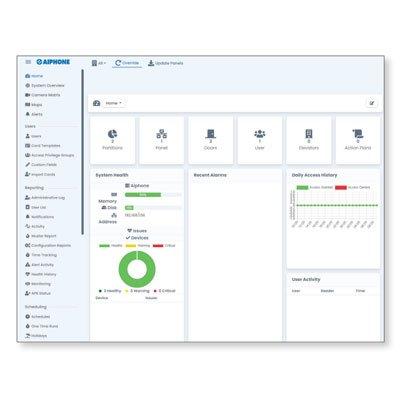
Small Business license of the AC Nio management software Manage a system of up to 80 doors and cameras, as well as elevators and unmanaged doors Allows up to five partitions and also supports Lightweight Directory Access Protocol (LDAP) integration
Add to Compare
Small Business license of the AC Nio management software Manage a system of up to 80 doors and cameras, as well as elevators and unmanaged doors Allows up to five partitions and also supports Lightweight Directory Access Protocol (LDAP) integration
Add to Compare
Management software for the AC Series access control system It is used to program a system and manage everyday functionality There are two license options - Essential license and Small Business license - available to accommodate different applications The Essential license can manage a system of up to 40 doors and cameras. It can be installed on a local server PC or on the AC-HOST embedded server The Small Business license can manage up to 80 doors and cameras, as well as elevators and unmanaged doors. This license allows up to five partitions and also supports Lightweight Directory Access Protocol (LDAP) integration
Add to Compare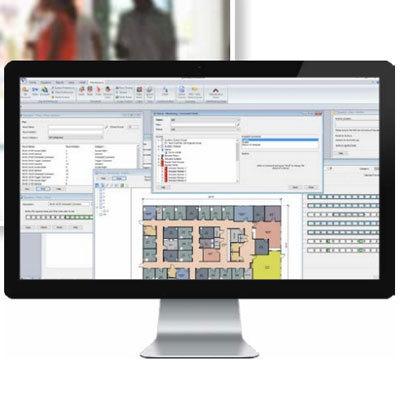
Designed to provide powerful access control and integrated security management solutions for most business applications Suitable for small to medium organisations requiring an access control and security management system that can use existing corporate networks Includes alarm management software, graphical maps, reports, a free video and visitor management system and many other powerful features In addition, a badge designer tool is included providing users with the ability to design and print identity badges Also includes database partitioning, which provides a cost-effective solution for buildings occupied by more than one organisation System access is also available from a web browser using the optional SymmetryWEB™ software Controls up to 512 card readers and 9 client computers as well as unlimited card holder capacity (10GB Max size database)
Add to Compare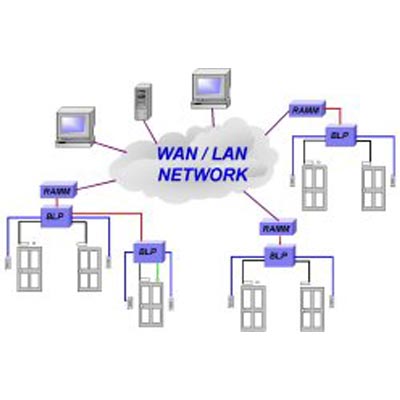
Security management software package for access control. Integrates with existing card readers and alarm monitoring devices. It features a distributed processing architecture that utilises remote intelligent control. Features operation on windows, supports up to 30/4 doors; 1,000/500 individual badge numbers; 50 access levels/10 access levels; multi-language support; single workstation and migration path to AXxess 202/NS. Applications inlucde office buildings, small commercial and manufacturing facilities.
Add to Compare