Access control systems & kits (1,016)

The Crypag perosnal card tag is an active radio device. Communication between tag and reader is scrambled. Battery low indication. Average key life 5 years or more (based on 6 minutes continuous use/day). 28g. Reading range dependent in aerial. One year guarantee against electronic failure.
Add to Compare
Inova PDC Multi format controller with integral keypad. Single door controller which supports magnetic stripe, wiegand and proximity readers. Alarm, tamper and unlock relays. RTE switch and exit reader inputs. RS485 data link. Various entry modes. Selectable door release times. Programming via on-board keypad or from on-line host. Non volatile memory. Provision for two readers enabling controlled entry and exit. Integral communications when linked to a PC or Inova PrintServer.
Add to Compare
Morse Watchmans Remote Box is a vailable in wall mount or desktop variations. It can replace the standard bottom mounted control box, or can be used in conjunction with the bottom mount control box so the system has a dual keypads and displays. It is useful for when the KeyWatcher needs to be mounted in a secure area such as a control room or vault and users need to be able to input their login information without entering the room.
Add to Compare
The 2100 Reader Inhibitor Module is used to disable a reader attached to the PAC 2100/1100 door controllers under certain conditions. It is designed to plug directly into a reader channel on the door controller and can be operated by anything which supplies a switching 12V (e.g. an alarm panel, mechanical switch etc.) at 20mA. A Reader Inhibitor is required for each reader to be disabled. When activated the Sig and RTE to the reader are broken and the reader disabled. Overrides such as breakglasses are not affected. Located in the door controller enclosure or other secure location. Five year guarantee against electronic failure.
Add to Compare
The Crypag perosnal card tag is an active radio device for fitting to vehicles. Communication between tag and reader is scrambled. Battery low indication. Average key life 5 years or more (based on 6 minutes continuous use/day). 28g. Reading range dependent in aerial. One year guarantee against electronic failure.
Add to Compare
This is essentially a powered version of the standard PAC ID device (electronic key/card), and is designed to be fitted to the underside of vehicles. It is a totally sealed potted construction suitable for underside vehicle mounting using either No 6 self-tapping screws or M4 bolts. The mounting centres on the transmitter are 84mm apart. Unique coding - 68 billion combinations. 5 year guarantee against electronic failure.
Add to Compare
The AIM Alarm Interface Module allows third party intruder alarm panels to be integrated with PAC access control systems without the need to modify the firmware of either system. The AIM allows you to use the access control system to specify who can arm/disarm the alarm system. Reduces false alarms as, when the system is armed, access to a building/area is restricted to those users who can disarm the system. Simplifies the arming/disarming procedure. Identifies who arms/disarms the system - each time a key is presented to a reader this is recorded by the access control system. Located in the door controller enclosure or other secure location. Five year guarantee against electronic failure.
Add to Compare
The PAC PIN Interface (with keypad) provides a means of adding extra security to installations using the PAC 2100/PAC 1100 door controllers. As well as using their PAC key/card (or other ID device) to gain access through a door, a 4-digit PIN number must also be entered. The PIN number is derived from the code stored in the key/card and cannot be changed. The use of a PIN may be optionally controlled by a time profile - i.e. at certain times/days the key or card only need be used, outside those hours the PIN must also be entered. Built in sounder to acknowledge key presses. Can be mounted up to 1000m from the door controller. Suitable for internal and external use. Five year guarantee against electronic failure.
Add to Compare
The PIN Interface without keypad is supplied with an 8-core flying lead, 2 metres in length. These can be connected to a suitable third party keypad. The keys of the keypad must be arranged into a three column by four row matrix, the keys themselves should have normally open contacts. It provides a means of adding extra security to installations using PAC 2100/PAC 1100 door controllers. As well as using their PAC key/card to gain access through a door, a 4-digit PIN number must also be entered. The PIN number is derived from the code stored in the key/card and cannot be changed. The use of a PIN may be optionally controlled by a time profile i.e. at certain times/days the key or card only need by used, outside those hours the PIN must also be entered. Built in sounder to acknowledge key presses. Can be mounted up to 1000m from the door controller. Suitable for internal and external use. Five year guarantee against electronic failure.
Add to Compare
Input/output module for use in auxiliary alarm or event applications. It has eight end of line inputs and 8 voltage free relay outputs. Can be mounted up to 1000 metres from its controller (PAC 1100/2100 & PAC 2200). White metal enclosure. 5 year guarantee against electronic failure.
Add to Compare
This is a potted module located in the door controller enclosure or other secure location. It is used to disable a reader under certain conditions. It can be used with any PAC door controller and can be operated by anything which supplies a switching 12V (e.g. and alarm panel, mechanical switch etc.) at 20mA. A Reader Inhibitor is required for each reader to be disabled. When activated the Sig and RTE to the reader are broken and the reader disabled. Overrides such as breakglasses are not affected. Five year guarantee against electronic failure.
Add to Compare
A fully supervised, addressable SDI/SDI2 bus device that allows access control integration for Bosch compatible control panels Direct interface to compatible Wiegand card readers On-board buzzer output and supervised on-board points Request to Exit and Request to Enter inputs that can have a shunt only option Four door states: Locked, Unlocked, Secured, Fire Unlock In a combination Fire/Intrusion system, it should not be used to lock doors used for emergency egress unless these doors have a mechanical release mechanism
Add to Compare
Nearly all access systems need a mains power outlet at the door. Fitting a mains spur for a new build can cost from £60, while retrofits can often cost more than £300. Most access control systems require cabinets to house power supplies and electronic circuit boards. These are often mounted above the door or in the ceiling void.Borer's new FUSION Access Control installation needs less hardware. A typical installation consists of a Borer smartcard reader, lock manager and electric lock all fitted at door handle height. The credit-card sized lock manager is mounted inside the Push-To-Exit switch or surface mounting, and is used to perform multiple functions including managing the power to the strike and monitor door status settings.FUSION needs less equipment to be installed and has fewer cables to terminate. You don't need mains power outlets at every door so you don't need a qualified electrician. As all equipment is mounted at door handle height, it can be safety installed without using ladders thereby eliminating the dangers and paperwork associated with working at heights.Many access control systems use traditional cable architecture to connect a chain of access doors to a PC or the LAN via an RS485 to Ethernet converted. The data cable is run from door to door in a daisy chain style. In contrast, FUSION uses standard CAT5e network cable. Each door has its own cable connection to a network bridge. More cable is needed, but CAT5e cable costs a third of the price of RS485 cable.Up to 80% of service calls are often resolved by simple power resetting equipment. FUSION has remote diagnostic and repair facilities built into the access control system. This enables many service tasks to be undertaken via remote control over the internet, using a secure connection. This can significantly impact on service overheads.FUSION supports power and data delivery over CAT5e network cable. This allows the system administrator or service provider to monitor, manage and control door access readers, attendance terminals and security input panels. In this way many basic faults can be resolved without having to call out a service engineer.FUSION can also significantly impact on your energy costs. Borer's door installation consisting of an electric strike and combined smartcard reader/controller using Power over Ethernet technology consumes only 3 watts, costing between £3 and £5 per annum for energy.
Add to Compare
Rosslare's convertible line unites its readers and stand-alones into one family, incorporating all products' functionalities, types and work modes. Following their successful integration, all products in this unique convertible line serve dual functionalities as both readers, and 500-user keypads. When connected to a Rosslare intelligent Secure Power Supply (PS-x15T or PS-x25T), each unit automatically converts into a full-feature 500-user access controller, with superior security due to the separation of keypad and the controller unit. The same product functions as a reader with diverse attributes when connected to a standard access controller, supporting 26-bit Wiegand, and Clock & Data and transmissions. All units are flexible to integrate, and offer further security by rejecting any wire tampering attempts.One stock, limitless possibilitiesFit for all access control applications from residential and commercial, to large-scale applications, our convertible product line is the answer to a wide variety of installations. Used in the home & in small businesses as an access control entrance keypad that extends the alarm system, or as readers in a large installation compatible with any access controllers - the options are indefinite. All the benefits of two-in-oneSecured operation - unreachable security using supervised digital communications to the keypad rejects wire tampering or power shortage attempts Large product range - from outdoor fully potted plastic units and metallic anti-vandal keypads, to new ultra-slim designer keypadsReduction of stock levels and inventory hassle - one product functions as twoTime savings - less products to learn and specialize in Money savings - in addition to manpower all units are priced same as readers, and the combined unit with power supply is priced as the stand-alone Common featuresFully-potted for outdoor usePatented, unique blue backlit illumination (some models)Built-In 125 KHz ASK EM Proximity card reader (some models)Highly-Sensitive optical back tamper and case tamper protection.Internal buzzer provides audible interface feedbackTwo Status / Programming Interface LED indication Lockout feature on wrong entries (Keypad / Card Tamper)
Add to Compare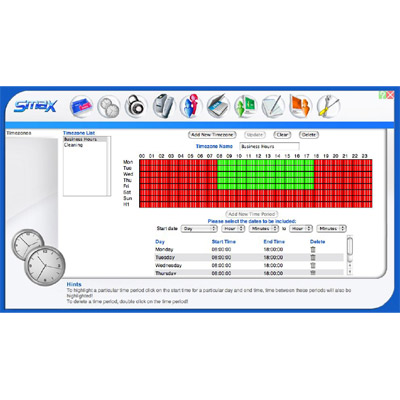
The IP based SMAX Access Control Management System From BQT is a sophisticated, intelligent and cost-effective security system, which manages the movement of staff and visitors within a building complex. SmaX can be managed and administered by any authorized individual, from any PC that has access to the network. The system is WEB browser based which means that the database and configuration remains within the SmaX hardware, offering a high level of data security and not requiring a dedicated PC. Individuals with the correct administration levels can manage remote sites from any location - obtaining reports, authorizing cards and changing access criteria, providing an ideal solution for multi site installations. Designed with the user in mind, setup and configuration are fast and the system is easy to manage - it's completely scalable and can be expanded as your needs grow. The SmaX management software enables the enrolment of Biometric and Mifare card Data at the click of a button, with the option of associating the cardholder photograph at the same time. The SmaX system has a single intelligent module to make the decisions at the door. Access permissions and transactions are carried out in these devices, which report directly to the main system in real time. If the Network fails at any point, these devices ensure system continuity without comprising security. Smax reduces the cost and stress involved in the management of staff and building security. New European website has been launched. To visit, click here.
Add to Compare
The EZ-32 Series are complete access control systems designed for fast and easy installation. All required components (software, controller, readers, UPS, backup battery and enclosure plus 2 test cards) are included in the package. The installer need only provide electrical locking devices and cabling to complete the installation. Compact 16 x 18 x 5 enclosure fits all components. 30,000 cardholders with 1MB of RAM. 1 auxiliary alarm input & 1 relay output per reader.
Add to Compare
A key cabinet designed to program and dispense up to 20 keys The keys are stored in the secured vault in an unprogrammed state until an approved PIN and/or RFID card is presented After the presentation of an approved PIN and/or RFID card the vault programs a key with that user’s access permissions and releases the door latch Reads the ID of most unencrypted 13.56 MHz RFID cards and recharges keys while in the vault The front of the vault contains an RFID reader with an indicator light and keypad, as well as an LCD touchscreen Can be scalable, meaning numerous vaults can communicate within a single CyberAudit Enterprise system Designed and developed to meet security needs of medium to large scale facilities
Add to Compare
The Reader interface to the personal computer via a standard USB cable (incorporated into the reader). One of the features of this reader is that it operates on a plug and play basis due to the USB standard it complies to. The reader works in conjunction with the Wavetrend Active RFID Tags. The enclosure was designed in such a way that it enhances the esthetical value of that individual’s desk. The user is able to select only one tag via software and monitor that specific tag, or monitor a few tags, which was selected by the user at installation.
Add to Compare
The EZ-Eight Series are complete access control systems designed for fast and easy installation. All required components (software, controller, readers, reader interfaces, UPS, backup battery, enclosure and 2 test cards) are included. The installer only needs to provide electrical locking devices and cabling to complete the installation. Compact 16 x 18 x 5 enclosure fits all components. 30,000 users with 1MB of RAM (included). 8 auxiliary alarm inputs & 8 relay outputs.
Add to Compare
WAVETREND’s unique logical PC access control system which provides personalised access for users authorised to use a particular computer. The Active Identification Tag transmits a unique code at constant intervals. The reader (plugged into the serial or USB port of the computer) then reports the presence of all tags in the environment to the control computer. Because each Tag has a unique code, the software can be configured to recognise specific codes. While the unique code is being read from an authorised tag, access to the computer is available. As soon as that unique tag is not present, the access control screensaver activates, hiding the information on the screen and restricting unauthorised access.
Add to Compare










